Hello my friend,
Probably you are already bored with data center stuff, but I’m writing about it again. The reason for that is very easy: it’s data center era now. With growth of cloud services and so on, we need to have more data centers, much more. That’s why I’m introducing interoperability between Nokia (Alcatel-Lucent) SR OS and new product in my lab, which is Arista EOS.
1 2 3 4 5 | No part of this blogpost could be reproduced, stored in a<br> retrieval system, or transmitted in any form or by any<br> means, electronic, mechanical or photocopying, recording,<br> or otherwise, for commercial purposes without the<br> prior permission of the author.<br> |
Brief description
Recently I was testing some features in Cumulus Linux and found out that they aren’t supported now, but they are on road map and will be supported in near future. So I started looking for another DC vendor in order to make the most use of my time. Very quickly I’ve found Arista, which seems to be good in enterprise and data center fields, according to the information from their website. Moreover, they have fully virtual switch or router vEOS, whatever we call it. There are two options available: for the lab and for the production. The lab vEOS is free of charge and you can download it from the website (link is provided in the bottom of the page) without a problem, you just need to create account at Arista website.
Some words about Arista EOS (after I have played with it a couple of hours). In a nutshell it’s Linux, but it also has its own CLI (for example, like Cumulus has), which is VERY Cisco-like. Especially Cisco IOS / IOS XE, rather than Cisco IOS XR or Cisco NX-OS.
If you have previous experience with Cisco IOS / IOS XE, this experience is very useful for Arista EOS.
Also Arista claims to support deployment over white boxes, what is also available for Cumulus Linux, but isn’t yet available for Nokia. I hope the latter could change.
Apart from that, it’s new networking vendor, we are going to get naked into our interoperability tests. Let’s get rock!
What we are going to test?
To save the time and give a kind of comparison, we’ll rebuild data centre, we have built with Cisco spines and pure Nokia (Alcatel-Lucent) SR OS based leafs or mixed Nokia (Alcatel-Lucent) SR OS with Cumulus Linux. Hence, we’ll deploy two scenarios:
- EVPN/VXLAN for pure L2 switching within broadcast domain
- EVPN/VXLAN for IRB (integrated routing and bridging) between 2 broadcast domains with anycast gateway. To be honest, anycast or not will be seen further, when we reach configuration of corresponding feature.
Software version
The following infrastructure is used in my lab:
- CentOS 7 with python 2.7.
- Ansible 2.4.2
- Nokia (Alcatel-Lucent) SR OS 15.0.R7
- Arista EOS 4.20.5F
- Cisco IOS XR 6.2.1
See the previous article to get details how to build the lab.
Topology
Physical topology doesn’t change from the previous lab; we just add additional node to the lab environment:
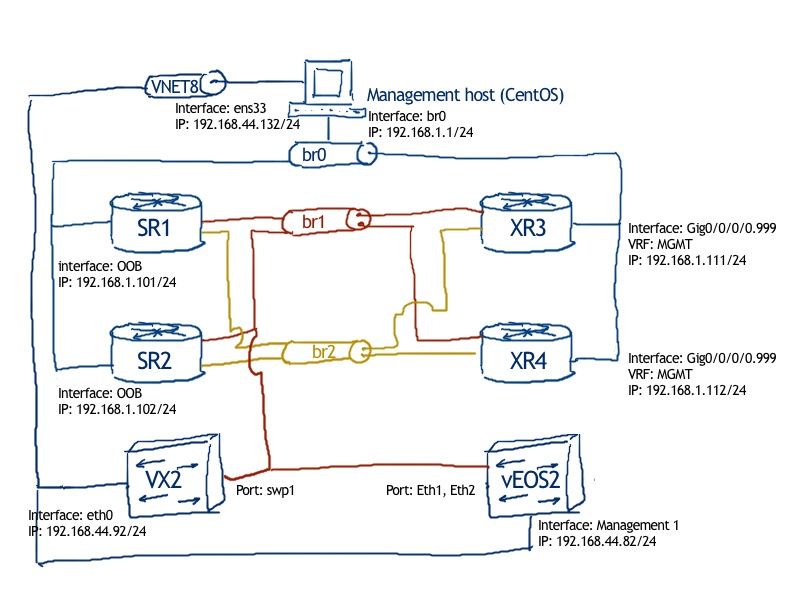
The following nodes are active: SR1, vEOS2, XR3 and XR4
In the logical topology, we follow exactly the same topology we have used previously with two spines (Cisco IOS XR) and two leafs (Nokia (Alcatel-Lucent) SR OS and Arista EOS):
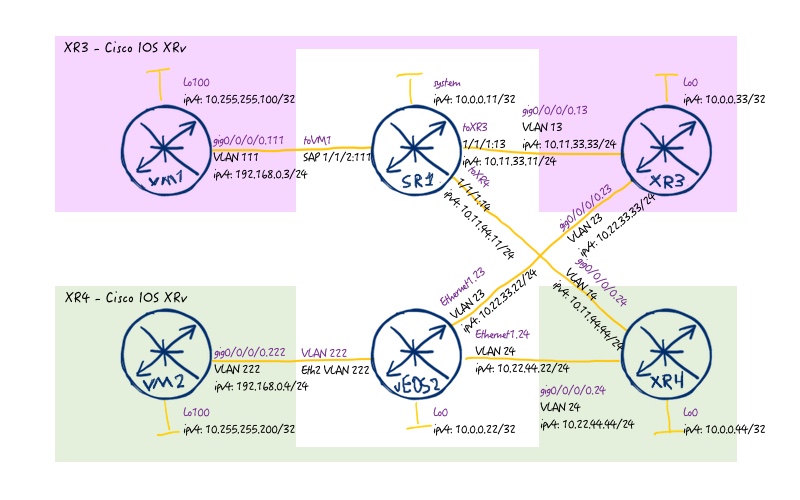
Like in the previous lab for Cumulus Linux, we start with preconfigured basic part on spine switches operated by Cisco IOS XR and basic configuration on the leaf switch operated by Nokia (Alcatel-Lucent) SR OS and no configuration on the second leaf by Arista EOS: 120_config_initial_linux 118_config_initial_SR1 118_config_initial_XR3 118_config_initial_XR4
Deployment of VM with Arista EOS and its initial configuration
As some times ago in the article about Cumulus Linux and Nokia SR OS interoperability for data centers, we start today with the installation of vEOS. You can download fully working Arista vEOS for lab absolutely officially from their website, you need just to create account with guest access:
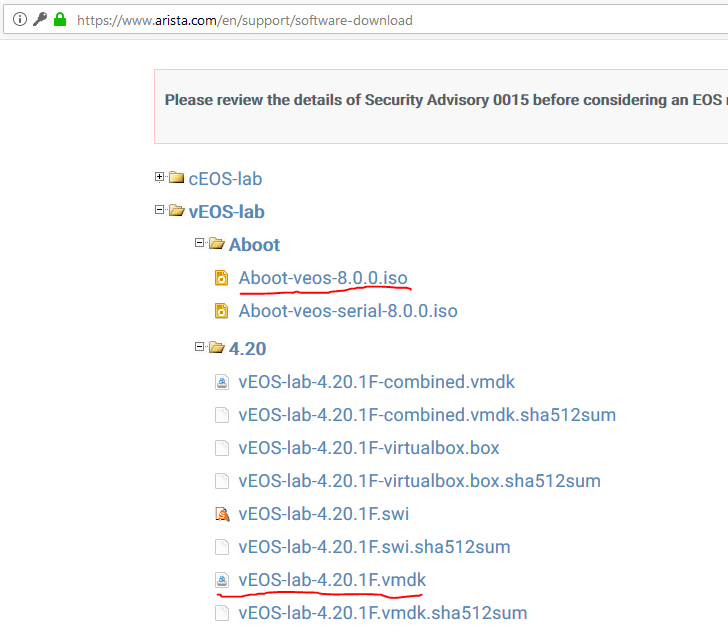
I have highlighted the files, I have downloaded myself and generally they are enough to launch Arista vEOS in our virtual data center testbed.
There are some guidelines in the official documentation, which we need to follow upon VM creation:
1 2 3 4 5 6 | <br> Hypervisor-agnostic Configuration<br> .<br> The Aboot-veos iso must be set as a CD-ROM image on the IDE bus, and the EOS vmdk must<br> be a hard drive image on the same IDE bus. The simulated hardware cannot contain a SATA<br> controller or vEOS will fail to fully boot.<br> |
In this example I’m using VMware Workstation 12 Player, though it can be launched on KVM as well.
So, let’s create the Arista vEOS.
#1. Create VM.

#2. Select install OS later.
#3. Select OS type
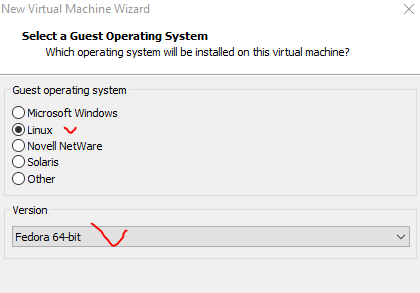
#4. Set name for VM
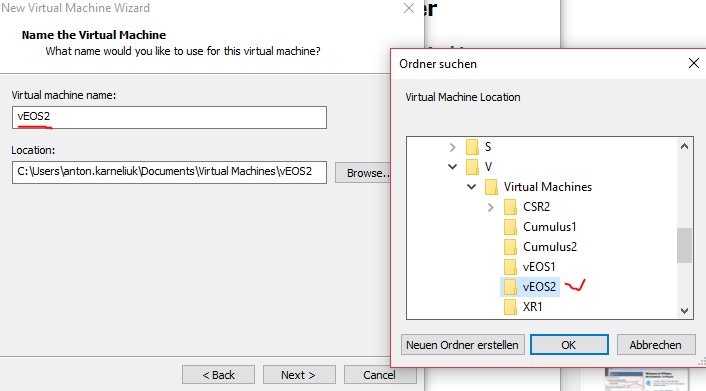
#5. Set disk type
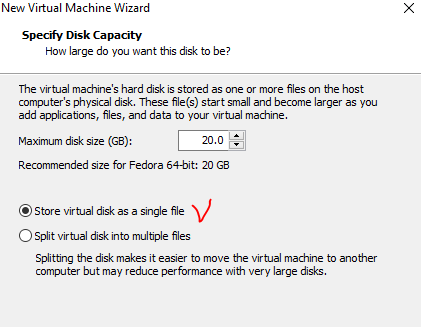
At this stage I can’t choose the existing VMDK image or even drive’s type. So I just point to create a single file, so that later I will replace it.
#6. Finish VM draft
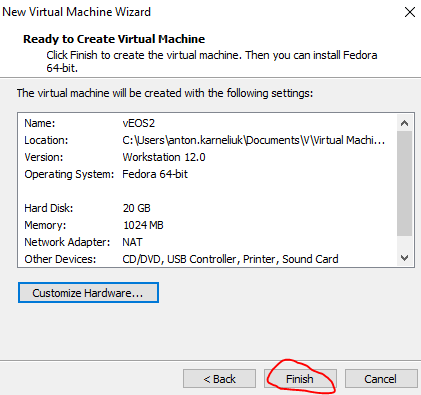
At this point we have created default VM (really default, as we haven’t chosen any Arista vEOS related files). Now we need to tune it and make it workable. So we make finish and then chose “Edit virtual machine settings” from main panel.
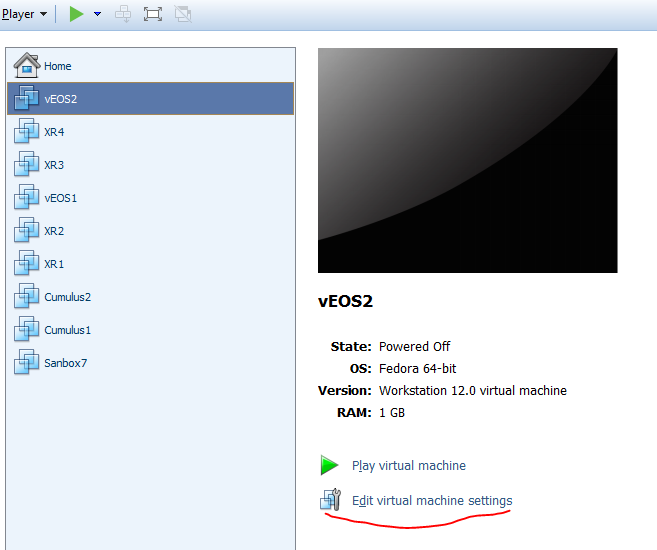
#7. Fine tuning – updating available memory
In the official documentation Arista proposes to have 2GB RAM per vEOS, so let’s provide it:
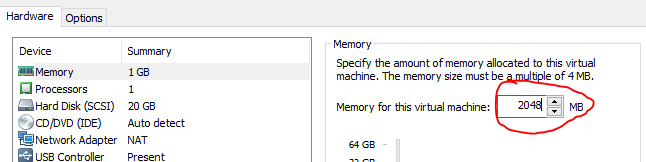
#8. Fine tuning – CPU virtualization
Don’t forget to enable VT-x:
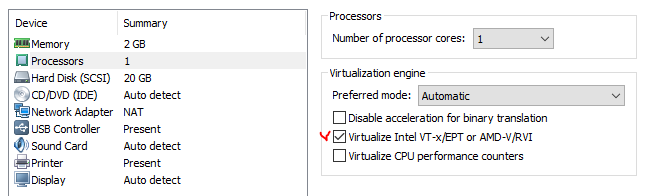
#9. Fine tuning – proper hard disk
Here we do several steps:
- In the folder with VM we copy downloaded in the beginning VMDK file
- Here in configuration we remove created drive
- Add new hard drive of IDE type and choosing copied VMDK
I don’t show the process of copying or removing as it’s self-explanatory. Here is the creation:
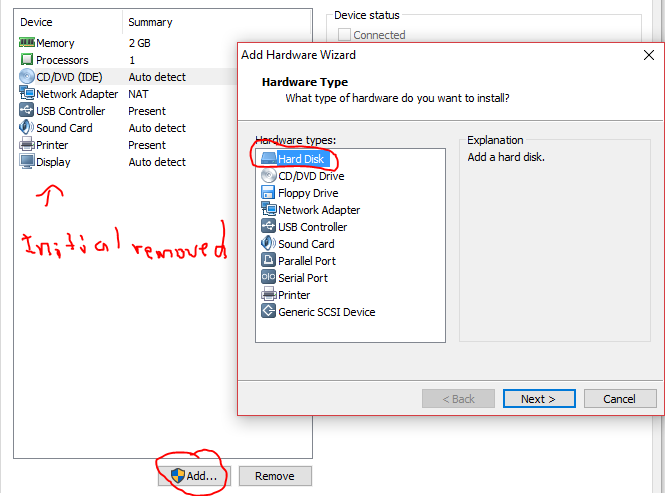
Choose of proper hard drive type:
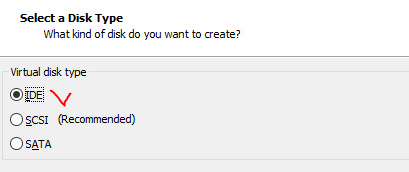
We’ll take the existing drive:
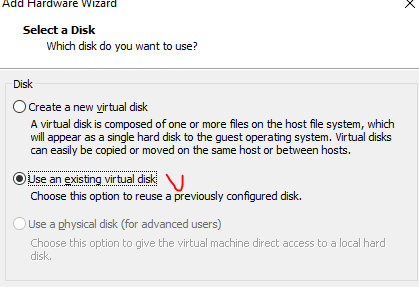
Finally we chose the copied disk:
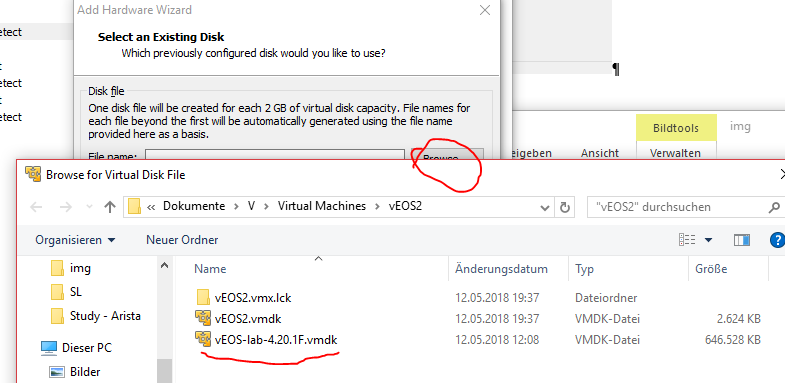
#10. Fine tuning – inserting disk in CD
As it’s said in the official documentation, we need to insert additional file into CD:
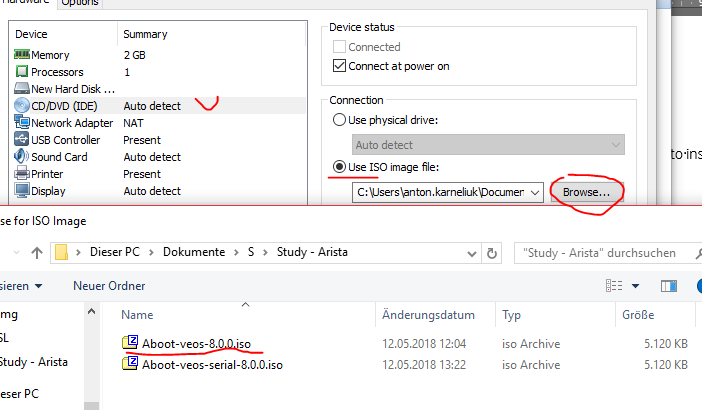
#11. Fine tuning – Network interfaces
The last point before the launch is the extending number of network interfaces. By default, only one interface is created, which is management one, much the same way we had in Cumulus Linux or even Nokia (Alcatel-Lucent) SR OS or Cisco IOS XR:
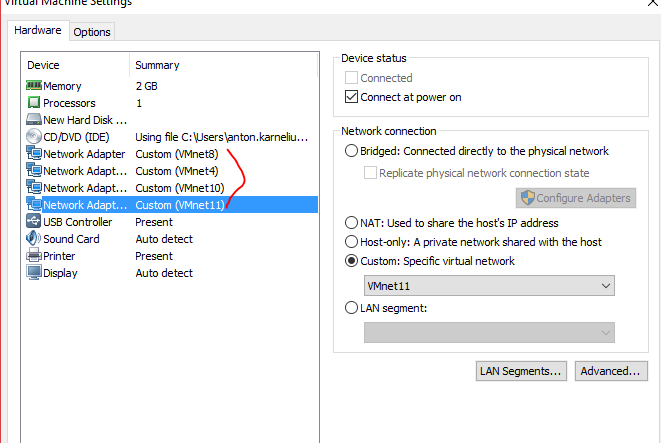
Our VM is created and ready for the first launch. I’m excited, and what about you?
If everything was done properly (according to the manual above), you will see Arista vEOS started booting:
It takes a couple of minutes to get started (longer that Cumulus VX but less than Nokia (Alcatel-Lucent) VSR and much less than Cisco IOS XRv). In a couple of minutes, you will see the invitation to login:
1 | localhost login: _ |
#12. Configuring username and management interface
Default login name is “admin” without password. It won’t work for SSH access, so we’ll have to create it as part of initial configuration. Let’s start with it and with the configuration if the management port, so that we can connect to Arista EOS with SSH:
Cisco fans, are you ready?!
1 2 3 4 5 6 7 8 9 | <br> localhost> enable<br> localhost# configure<br> localhost(config)# username aaa privilege 15 secret aaa<br> localhost(config)# interface management 1<br> localhost(config-if-Ma1)# ip address 192.168.44.82/24<br> localhost(config-if-Ma1)# hostname vEOS2<br> localhost(config)# end<br> localhost# write memory<br> |
Don’t forget to save configuration by “write memory” after all changes.
Now we are able to connect to Arista EOS leaf switch vEOS2 using SSH client, like Putty:
1 2 3 4 5 | <br> login as: aaa<br> Using keyboard-interactive authentication.<br> Password:<br> vEOS2><br> |
#13. Configuring connectivity with the rest of the data centre fabric
The last topic on initial agenda is the configuration of connectivity to other devices in our data centre, fabric, more precisely two spine switches based on Cisco IOS XR:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | <br> .vEOS2#show run<br> .! Command: show running-config<br> .! device: vEOS2 (vEOS, EOS-4.20.1F)<br> .!<br> .interface Ethernet1<br> . no switchport<br> .!<br> .interface Ethernet1.23<br> . logging event link-status<br> . encapsulation dot1q vlan 23<br> . ip address 10.22.33.22/24<br> .!<br> .interface Ethernet1.24<br> . logging event link-status<br> . encapsulation dot1q vlan 24<br> . ip address 10.22.44.22/24<br> .!<br> |
Only relevant part of the configuration is shown
Let’s check the reachability of spine switches:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | <br> vEOS2#ping 10.22.33.33<br> PING 10.22.33.33 (10.22.33.33) 72(100) bytes of data.<br> 80 bytes from 10.22.33.33: icmp_seq=1 ttl=255 time=15.5 ms<br> 80 bytes from 10.22.33.33: icmp_seq=2 ttl=255 time=10.4 ms<br> 80 bytes from 10.22.33.33: icmp_seq=3 ttl=255 time=8.37 ms<br> 80 bytes from 10.22.33.33: icmp_seq=4 ttl=255 time=9.03 ms<br> 80 bytes from 10.22.33.33: icmp_seq=5 ttl=255 time=8.28 ms<br> --- 10.22.33.33 ping statistics ---<br> 5 packets transmitted, 5 received, 0% packet loss, time 58ms<br> rtt min/avg/max/mdev = 8.289/10.333/15.533/2.712 ms, ipg/ewma 14.590/12.805 ms<br> .<br> .<br> vEOS2#ping 10.22.44.44<br> PING 10.22.44.44 (10.22.44.44) 72(100) bytes of data.<br> 80 bytes from 10.22.44.44: icmp_seq=1 ttl=255 time=13.2 ms<br> 80 bytes from 10.22.44.44: icmp_seq=2 ttl=255 time=11.1 ms<br> 80 bytes from 10.22.44.44: icmp_seq=3 ttl=255 time=9.37 ms<br> 80 bytes from 10.22.44.44: icmp_seq=4 ttl=255 time=9.22 ms<br> 80 bytes from 10.22.44.44: icmp_seq=5 ttl=255 time=7.30 ms<br> --- 10.22.44.44 ping statistics ---<br> 5 packets transmitted, 5 received, 0% packet loss, time 58ms<br> rtt min/avg/max/mdev = 7.302/10.211/13.234/2.712 ms, ipg/ewma 14.590/12.805 ms<br> |
As basic connectivity is established, we go further with BGP configuration.
BGP configuration of leaf switches (Nokia (Alcatel-Lucent) SR OS and Cumulus Linux)
Following the same approach, we have for building data center fabric with Cumulus Linux and Nokia (Alcatel-Lucent) SR OS, we have to major building blocks for BGP:
- Configuration of BGP for underlay IP fabric
- Configuration of BGP for overlay EVPN
BGP-based underlay IP fabric
We build already well-known topology for BGP:
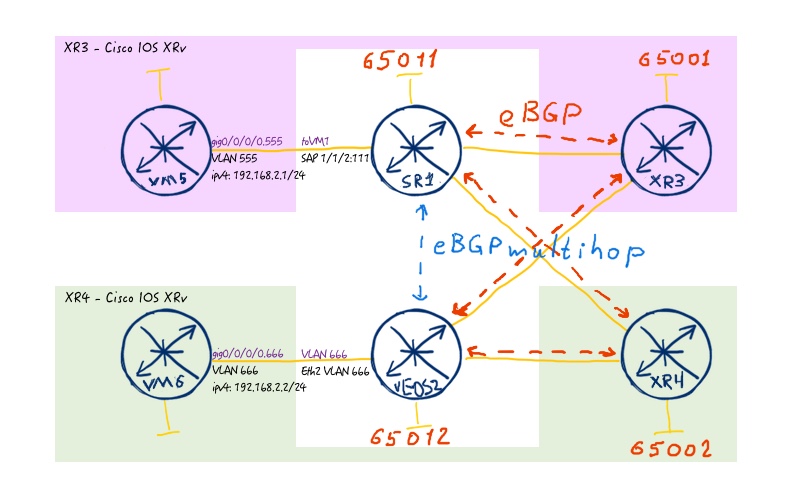
Configuration of BGP for Nokia (Alcatel-Lucent) SR OS is coming from previous articles (link), so we hope you understand it well already. The new one is coming for Arista EOS:
| SR1 – Nokia (Alcatel-Lucent) VSR | vEOS2 – Arista EOS |
|
A:SR1>edit-cfg# candidate view |
vEOS2#show run |
Command “service routing protocols model multi-agent” is of particular importance. If don’t enter it, you won’t be able to configure EVPN address family
Actually configuration of BGP in Arista EOS is very similar to one in Cisco, even in Cisco IOS XR (link), so it’s easy for us, as we have configured it many times. In the example, we just create eBGP peering on interface level between leaf and spine switches. Let’s check these BGP sessions. We start at Arista EOS leaf switch vEOS1:
1 2 3 4 5 6 7 8 | <br> .vEOS2#show bgp ipv4 unicast summary<br> .BGP summary information for VRF default<br> .Router identifier 10.0.0.22, local AS number 65012<br> .Neighbor Status Codes: m - Under maintenance<br> . Neighbor V AS MsgRcvd MsgSent InQ OutQ Up/Down State PfxRcd PfxAcc<br> . 10.22.33.33 4 65001 23 21 0 0 00:12:35 Estab 3 3<br> . 10.22.44.44 4 65002 22 24 0 0 00:13:11 Estab 3 3<br> |
At Nokia (Alcatel-Lucent) SR OS:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <br> .A:SR1# show router bgp summary<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> .BGP Summary<br> .===============================================================================<br> .Legend : D - Dynamic Neighbor<br> .===============================================================================<br> .Neighbor<br> .Description<br> . AS PktRcvd InQ Up/Down State|Rcv/Act/Sent (Addr Family)<br> . PktSent OutQ<br> .-------------------------------------------------------------------------------<br> .10.11.33.33<br> . 65001 58 0 00h26m03s 2/2/4 (IPv4)<br> . 62 0<br> .10.11.44.44<br> . 65002 58 0 00h24m07s 2/2/4 (IPv4)<br> . 68 0<br> .-------------------------------------------------------------------------------<br> |
BGP peering is established as proper and we see some routes being propagated. It’s very easy to guess that these are our loopbacks, but let’s double check that:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | <br> .vEOS2#show bgp ipv4 unicast<br> .BGP routing table information for VRF default<br> .Router identifier 10.0.0.22, local AS number 65012<br> .Route status codes: s - suppressed, * - valid, > - active, # - not installed, E - ECMP head, e - ECMP<br> . S - Stale, c - Contributing to ECMP, b - backup, L - labeled-unicast<br> . % - Pending BGP convergence<br> .Origin codes: i - IGP, e - EGP, ? - incomplete<br> .AS Path Attributes: Or-ID - Originator ID, C-LST - Cluster List, LL Nexthop - Link Local Nexthop<br> .<br> . Network Next Hop Metric LocPref Weight Path<br> . * > 10.0.0.11/32 10.22.33.33 - 100 0 65001 65011 i<br> . * > 10.0.0.22/32 - - - 0 i<br> . * > 10.0.0.33/32 10.22.33.33 0 100 0 65001 i<br> |
And from Nokia prospective we will also check BGP RIB, but you remember locally advertised routes are shown there:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | <br> .A:SR1# show router bgp routes ipv4<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> . Legend -<br> . Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid<br> . l - leaked, x - stale, > - best, b - backup, p - purge<br> . Origin codes : i - IGP, e - EGP, ? - incomplete<br> .<br> .===============================================================================<br> .BGP IPv4 Routes<br> .===============================================================================<br> .Flag Network LocalPref MED<br> . Nexthop (Router) Path-Id Label<br> . As-Path<br> .-------------------------------------------------------------------------------<br> .u*>i 10.0.0.22/32 None None<br> . 10.11.33.33 None -<br> . 65001 65012<br> .u*>i 10.0.0.33/32 None 0<br> . 10.11.33.33 None -<br> . 65001<br> .-------------------------------------------------------------------------------<br> .Routes : 2<br> .===============================================================================<br> |
So, control plane looks fine for our underlay data centre fabric, and before we move further we check that data plane works as well. How will we do that? By utilizing one of the most powerful tool in network engineer’s toolkit:
1 2 3 4 5 6 7 8 9 10 11 | <br> vEOS2#ping 10.0.0.11 source 10.0.0.22<br> PING 10.0.0.11 (10.0.0.11) from 10.0.0.22 : 72(100) bytes of data.<br> 80 bytes from 10.0.0.11: icmp_seq=1 ttl=63 time=40.7 ms<br> 80 bytes from 10.0.0.11: icmp_seq=2 ttl=63 time=18.7 ms<br> 80 bytes from 10.0.0.11: icmp_seq=3 ttl=63 time=18.6 ms<br> 80 bytes from 10.0.0.11: icmp_seq=4 ttl=63 time=23.0 ms<br> 80 bytes from 10.0.0.11: icmp_seq=5 ttl=63 time=18.7 ms<br> --- 10.0.0.11 ping statistics ---<br> 5 packets transmitted, 5 received, 0% packet loss, time 152ms<br> rtt min/avg/max/mdev = 18.620/23.984/40.798/8.574 ms, ipg/ewma 38.099/32.126 ms<br> |
BGP-based overlay EVPN
The next step in our journey is to establish multihop eBGP peering between Nokia (Alcatel-Lucent) SR OS leaf SR1 and Arista EOS lead vEOS2 with the following topology:

To do that we implement the configuration below:
| SR1 – Nokia (Alcatel-Lucent) VSR | vEOS2 – Arista EOS |
|
A:SR1>edit-cfg# candidate view |
vEOS2#show run |
Also the configuration is relatively easy. There is one point specific to Arista EOS (at least it’s shown in the official config guide), which is activation of extended communities so that they are sent to neighbour. In Nokia (Alcatel-Lucent) or Cisco IOS XR or Cumulus Linux it’s done automatically, though in Cisco IOS you need to manually activate that.
Different vendors mean different default behaviour, just know what exactly needed technologywise and implement that.
For now we can check only the status of BGP peering for EVPN, as we haven’t advertised anything yet. In Arista EOS the command is the following:
1 2 3 4 5 6 7 | <br> .vEOS2#show bgp evpn summary<br> .BGP summary information for VRF default<br> .Router identifier 10.0.0.22, local AS number 65012<br> .Neighbor Status Codes: m - Under maintenance<br> . Neighbor V AS MsgRcvd MsgSent InQ OutQ Up/Down State PfxRcd PfxAcc<br> . 10.0.0.11 4 65011 22 23 0 0 00:06:55 Estab 0 0<br> |
In Nokia (Alcatel-Lucent) we just use the same command we have used previously for checking BGP session for IPv4 unicast address family, but this time we extend it with address family:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | <br> .A:SR1# show router bgp summary family evpn<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> .!<br> .! Output is ommited<br> .!<br> .===============================================================================<br> .BGP EVPN Summary<br> .===============================================================================<br> .Legend : D - Dynamic Neighbor<br> .===============================================================================<br> .Neighbor<br> . AS PktRcvd PktSent InQ OutQ Up/Down State|Recv/Actv/Sent<br> .-------------------------------------------------------------------------------<br> .10.0.0.22<br> . 65012 30 25 0 0 00h09m44s 0/0/0<br> .-------------------------------------------------------------------------------<br> |
At this point we consider that data centre fabric, both underlay and overlay, is fully ready and we can proceed with customer’s use cases.
Case #1. Switching within L2 domain (L2 option of EVPN with VXLAN)
We start out journey to EVPN/VXLAN use cases with building switching domain across two leafs, hence pure L2 use case with the following topology:
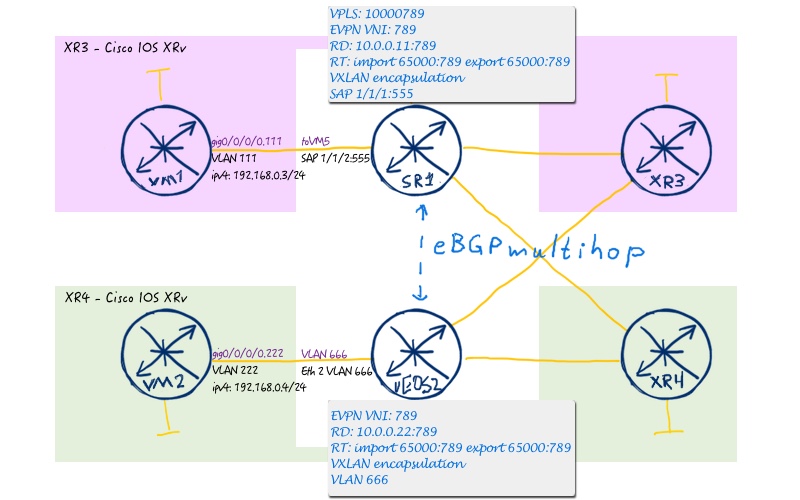
The configuration below is necessary to be applied at both our leaf switches by Nokia (Alcatel-Lucent) SR OS and Arista EOS:
| SR1 – Nokia (Alcatel-Lucent) VSR | vEOS2 – Arista EOS |
|
A:SR1>edit-cfg# candidate view |
vEOS2#show run |
Here we can see at a glance two difference logic of the configuration. In Nokia (Alcatel-Lucent) SR OS all the configuration related to particular service, like here we speak about particular EVPN service, is contained without single configuration context. In Arista EOS, much like we’ve seen recently in Cumulus Linux (link), the configuration of EVPN service is splitted across VLAN, interface VXLAN, which contains both VTEP address and VNI to VLAN mapping, and BGP context, where we assign RD/RT and inform BGP to distribute learned MAC addresses.
On control plane we check the BGP RIB for EVPN. On Arista EOS we use the following command:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <br> .vEOS2#show bgp evpn vni 789<br> .BGP routing table information for VRF default<br> .Router identifier 10.0.0.22, local AS number 65012<br> .Route status codes: s - suppressed, * - valid, > - active, # - not installed, E - ECMP head, e - ECMP<br> . S - Stale, c - Contributing to ECMP, b - backup<br> . % - Pending BGP convergence<br> .Origin codes: i - IGP, e - EGP, ? - incomplete<br> .AS Path Attributes: Or-ID - Originator ID, C-LST - Cluster List, LL Nexthop - Link Local Nexthop<br> .<br> . Network Next Hop Metric LocPref Weight Path<br> . * > RD: 10.0.0.11:789 mac-ip 0050.5623.b334<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:789 mac-ip 0265.ff00.033a<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.22:789 mac-ip faac.a614.0103<br> . - - - 0 i<br> . * > RD: 10.0.0.11:789 imet 10.0.0.11<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.22:789 imet 10.0.0.22<br> . - - - 0 i<br> |
We see 5 routes: 2 of them are type 3 routes, which are announced by VTEPs and used for BUM traffic, 3 of them are host routes. Why do we have 3 type-2 routes? 2 of them, marked with bold are MAC addresses of our VMs, whereas third one comes into play-based on the fact we have enabled proxy-arp as this MAC relates to SR 7750 chassis:
1 2 3 | <br> .A:SR1# show chassis | match MAC<br> . Base MAC address : 02:65:ff:00:00:00<br> |
At Nokia (Alcatel-Lucent) SR OS we can see BGP RIB for incoming routes and separately BGP-RIB-OUT for routes being sent to neighbors.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 | <br> .A:SR1# show router bgp routes evpn mac<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> . Legend -<br> . Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid<br> . l - leaked, x - stale, > - best, b - backup, p - purge<br> . Origin codes : i - IGP, e - EGP, ? - incomplete<br> .<br> .===============================================================================<br> .BGP EVPN MAC Routes<br> .===============================================================================<br> .Flag Route Dist. MacAddr ESI<br> . Tag Mac Mobility Label1<br> . Ip Address<br> . NextHop<br> .-------------------------------------------------------------------------------<br> .u*>i 10.0.0.22:789 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 789<br> . N/A<br> . 10.0.0.22<br> .<br> .-------------------------------------------------------------------------------<br> .Routes : 1<br> .===============================================================================<br> .<br> .<br> .A:SR1# show router bgp neighbor 10.0.0.22 advertised-routes evpn mac<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> . Legend -<br> . Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid<br> . l - leaked, x - stale, > - best, b - backup, p - purge<br> . Origin codes : i - IGP, e - EGP, ? - incomplete<br> .<br> .===============================================================================<br> .BGP EVPN MAC Routes<br> .===============================================================================<br> .Flag Route Dist. MacAddr ESI<br> . Tag Mac Mobility Label1<br> . Ip Address<br> . NextHop<br> .-------------------------------------------------------------------------------<br> .i 10.0.0.11:789 00:50:56:23:b3:34 ESI-0<br> . 0 Seq:0 VNI 789<br> . N/A<br> . 10.0.0.11<br> .<br> .i 10.0.0.11:789 02:65:ff:00:03:3a ESI-0<br> . 0 Static VNI 789<br> . N/A<br> . 10.0.0.11<br> .<br> .i 10.0.0.22:789 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 789<br> . N/A<br> . 10.0.0.22<br> .<br> .-------------------------------------------------------------------------------<br> .Routes : 3<br> .===============================================================================<br> |
Control plane looks OK, what is good sign. Now we see into data plane to double check that. At Arista EOS we have two commands for that, which show a bit different but mainly similar information:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | <br> .vEOS2#show mac address-table vlan 666<br> . Mac Address Table<br> .------------------------------------------------------------------<br> .<br> .Vlan Mac Address Type Ports Moves Last Move<br> .---- ----------- ---- ----- ----- ---------<br> . 666 0050.5623.b334 DYNAMIC Vx1 1 0:02:34 ago<br> . 666 0265.ff00.033a STATIC Vx1<br> . 666 faac.a614.0103 DYNAMIC Et2 1 0:04:06 ago<br> .Total Mac Addresses for this criterion: 3<br> .<br> .<br> .vEOS2#show vxlan address-table<br> . Vxlan Mac Address Table<br> .----------------------------------------------------------------------<br> .<br> .VLAN Mac Address Type Prt VTEP Moves Last Move<br> .---- ----------- ---- --- ---- ----- ---------<br> . 666 0050.5623.b334 EVPN Vx1 10.0.0.11 1 0:02:54 ago<br> . 666 0265.ff00.033a DYNAMIC Vx1 10.0.0.11 1 0:02:54 ago<br> .Total Remote Mac Addresses for this criterion: 2<br> |
As Nokia (Alcatel-Lucent) follows service-oriented model, so we check the forwarding database per service:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | <br> .A:SR1# show service id 1000789 fdb detail<br> .<br> .===============================================================================<br> .Forwarding Database, Service 1000789<br> .===============================================================================<br> .ServId MAC Source-Identifier Type Last Change<br> . Age<br> .-------------------------------------------------------------------------------<br> .1000789 00:50:56:23:b3:34 sap:1/1/2:555 L/135 05/13/18 09:54:58<br> .1000789 fa:ac:a6:14:01:03 vxlan: Evpn 05/13/18 09:56:25<br> . 10.0.0.22:789<br> .-------------------------------------------------------------------------------<br> .No. of MAC Entries: 2<br> .-------------------------------------------------------------------------------<br> .Legend: L=Learned O=Oam P=Protected-MAC C=Conditional S=Static<br> .===============================================================================<br> |
The outputs from different commands looks nice and we need to do the last thing on this verification path
Case #1. Verification
As usual we test our data plane by issuing ping command between our VMs:
1 2 3 4 5 6 7 | <br> RP/0/0/CPU0:XR3#ping vrf VM5 192.168.2.2<br> Sat May 12 23:23:40.999 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 99/259/409 ms<br> |
Configuration of Cisco IOS XR to emulate VMs as well as packet capture is provided in one of the previous articles
Case #2. Inter-VXLAN routing (L3 option of EVPN with VXLAN – distributed gateway)
Going further, we deploy asymmetric IRB, or inter VXLAN routing, with the aim to deploy anycast gateway at both Nokia (Alcatel-Lucent) SR OS and Arista EOS leafs to provide possibility of two broadcast domains talk to each other. The image below shows broadcast domain 1:
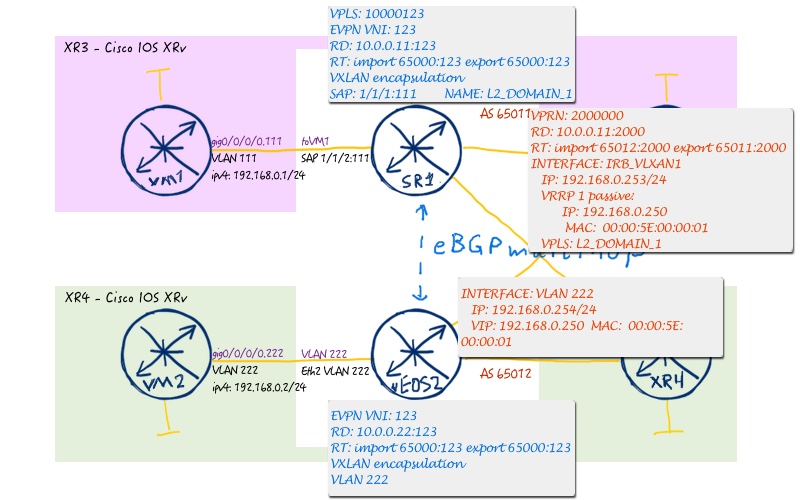
And the next one image reflects domain 2:
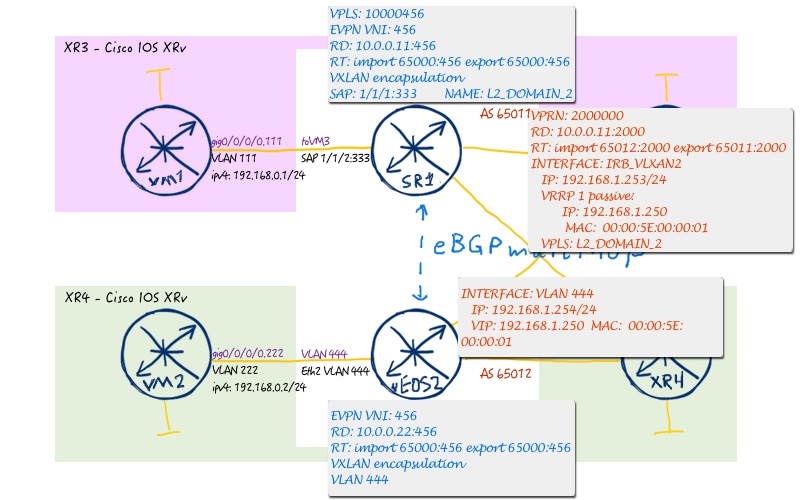
The following configuration must be implemented:
| SR1 – Nokia (Alcatel-Lucent) VSR | vEOS2 – Arista EOS |
|
A:SR1>edit-cfg# candidate view |
vEOS2#show run |
In Nokia (Alcatel-Lucent) SR OS we create two L2 domains within VPLS context and map them to L3 instance, which is called VPRN in Nokia (Alcatel-Lucent) SR OS.
More information about Nokia (Alcatel-Lucent) VPRN you will find in the dedicated article.
What is important, we deploy distributed anycast GW configuration, shared by @Jorge Rabadan, and you will see later on, that this configuration works interoperable with distributed anycast GW from Arista EOS! That’s really amazing!
In Arista EOS, comparing to configuration of L2 EVPN service, we add VLAN interfaces with IP addresses and virtual-address for anycast GW as well as corresponding VRF, where we map the customer. To make distributed anycast GW working we configure the same MAC address for virtual instances both at Nokia (Alcatel-Lucent) SR OS and Arista EOS leaf switches.
We begin our verifications traditionally with BGP RIB for EVPN:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 | <br> .vEOS2#show bgp evpn<br> .BGP routing table information for VRF default<br> .Router identifier 10.0.0.22, local AS number 65012<br> .Route status codes: s - suppressed, * - valid, > - active, # - not installed, E - ECMP head, e - ECMP<br> . S - Stale, c - Contributing to ECMP, b - backup<br> . % - Pending BGP convergence<br> .Origin codes: i - IGP, e - EGP, ? - incomplete<br> .AS Path Attributes: Or-ID - Originator ID, C-LST - Cluster List, LL Nexthop - Link Local Nexthop<br> .<br> . Network Next Hop Metric LocPref Weight Path<br> . * > RD: 10.0.0.11:123 mac-ip 0000.5e00.0001 192.168.0.250<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:456 mac-ip 0000.5e00.0001 192.168.1.250<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:123 mac-ip 0020.0001.2301 192.168.0.253<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:456 mac-ip 0020.0004.5601 192.168.1.253<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:123 mac-ip 0050.5623.b334<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:456 mac-ip 0050.5623.b334<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:789 mac-ip 0050.5623.b334<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:789 mac-ip 0265.ff00.033a<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.22:123 mac-ip faac.a614.0103<br> . - - - 0 i<br> . * > RD: 10.0.0.22:456 mac-ip faac.a614.0103<br> . - - - 0 i<br> . * > RD: 10.0.0.22:123 mac-ip faac.a614.0103 192.168.0.2<br> . - - - 0 i<br> . * > RD: 10.0.0.22:456 mac-ip faac.a614.0103 192.168.1.2<br> . - - - 0 i<br> . * > RD: 10.0.0.11:123 imet 10.0.0.11<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:456 imet 10.0.0.11<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.11:789 imet 10.0.0.11<br> . 10.0.0.11 - 100 0 65011 i<br> . * > RD: 10.0.0.22:123 imet 10.0.0.22<br> . - - - 0 i<br> . * > RD: 10.0.0.22:456 imet 10.0.0.22<br> . - - - 0 i<br> . * > RD: 10.0.0.22:789 imet 10.0.0.22<br> . - - - 0 i<br> |
Based on route distinguisher we can understand, which routes are related to particular VNIs, though we can extend command, like “show bgp evpn vni xxx”, to see all the routes belonging to interested VRF.
In Nokia (Alcatel-Lucent) SR OS we check to BGP RIB for EVPN as well:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 | <br> .A:SR1# show router bgp routes evpn mac<br> .===============================================================================<br> . BGP Router ID:10.0.0.11 AS:65011 Local AS:65011<br> .===============================================================================<br> . Legend -<br> . Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid<br> . l - leaked, x - stale, > - best, b - backup, p - purge<br> . Origin codes : i - IGP, e - EGP, ? - incomplete<br> .<br> .===============================================================================<br> .BGP EVPN MAC Routes<br> .===============================================================================<br> .Flag Route Dist. MacAddr ESI<br> . Tag Mac Mobility Label1<br> . Ip Address<br> . NextHop<br> .-------------------------------------------------------------------------------<br> .i 10.0.0.11:123 00:20:00:01:23:01 ESI-0<br> . 0 Static VNI 123<br> . 192.168.0.253<br> . 10.0.0.11<br> .<br> .i 10.0.0.11:456 00:20:00:04:56:01 ESI-0<br> . 0 Static VNI 456<br> . 192.168.1.253<br> . 10.0.0.11<br> .<br> .i 10.0.0.11:789 00:50:56:23:b3:34 ESI-0<br> . 0 Seq:0 VNI 789<br> . N/A<br> . 10.0.0.11<br> .<br> .i 10.0.0.11:789 02:65:ff:00:03:3a ESI-0<br> . 0 Static VNI 789<br> . N/A<br> . 10.0.0.11<br> .<br> .u*>i 10.0.0.22:123 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 123<br> . 192.168.0.2<br> . 10.0.0.22<br> .<br> .u*>i 10.0.0.22:123 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 123<br> . N/A<br> . 10.0.0.22<br> .<br> .u*>i 10.0.0.22:456 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 456<br> . 192.168.1.2<br> . 10.0.0.22<br> .<br> .u*>i 10.0.0.22:456 fa:ac:a6:14:01:03 ESI-0<br> . 0 Seq:0 VNI 456<br> . N/A<br> . 10.0.0.22<br> .<br> .-------------------------------------------------------------------------------<br> .Routes : 8<br> .===============================================================================<br> |
As you see, the amount of routes are less due to Nokia (Alcatel-Lucent) SR OS behaviour, we have explained previously,
We won’t check the MAC address table in this case, as we did in in the first case and it shew correct output. Here we’ll check two more things. The first one is related to ARP to check that all the tables are build correctly.
Nokia (Alcatel-Lucent) SR OS:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | <br> .A:SR1# show router 20000000 arp<br> .===============================================================================<br> .ARP Table (Service: 20000000)<br> .===============================================================================<br> .IP Address MAC Address Expiry Type Interface<br> .-------------------------------------------------------------------------------<br> .192.168.0.1 00:50:56:23:b3:34 02h41m34s Dyn[I] IRB_VXLAN1<br> .192.168.0.250 00:00:5e:00:00:01 00h00m00s Oth[I] IRB_VXLAN1<br> .192.168.0.253 00:20:00:01:23:01 00h00m00s Oth[I] IRB_VXLAN1<br> .192.168.0.254 00:50:56:63:f3:eb 02h41m40s Dyn[I] IRB_VXLAN1<br> .192.168.1.1 00:50:56:23:b3:34 02h41m39s Dyn[I] IRB_VXLAN2<br> .192.168.1.250 00:00:5e:00:00:01 00h00m00s Oth[I] IRB_VXLAN2<br> .192.168.1.253 00:20:00:04:56:01 00h00m00s Oth[I] IRB_VXLAN2<br> .192.168.1.254 00:50:56:63:f3:eb 02h41m48s Dyn[I] IRB_VXLAN2<br> .-------------------------------------------------------------------------------<br> .No. of ARP Entries: 8<br> .===============================================================================<br> |
Arista EOS:
1 2 3 4 5 6 7 8 9 | <br> .vEOS2#show arp vrf CUST<br> .Address Age (min) Hardware Addr Interface<br> .192.168.0.1 N/A 0050.5623.b334 Vlan222, Vxlan1<br> .192.168.0.2 N/A faac.a614.0103 Vlan222, Ethernet2<br> .192.168.0.253 - 0020.0001.2301 Vlan222, Vxlan1<br> .192.168.1.1 N/A 0050.5623.b334 Vlan444, Vxlan1<br> .192.168.1.2 N/A faac.a614.0103 Vlan444, Ethernet2<br> .192.168.1.253 - 0020.0004.5601 Vlan444, Vxlan1<br> |
And the last verification, before we jump to actual packets’ transmission, is to show the operation of component related to distributed anycast GW.
Arista EOS:
1 2 3 4 5 6 | <br> .vEOS2(config-if-Vl222)#show active<br> .interface Vlan222<br> . vrf forwarding CUST<br> . ip address 192.168.0.254/24<br> . ip virtual-router address 192.168.0.250<br> |
Nokia (Alcatel-Lucent) SR OS:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | <br> .A:SR1# show router 20000000 vrrp instance<br> .===============================================================================<br> .VRRP Instances<br> .===============================================================================<br> .Interface Name VR Id Own Adm State Base Pri Msg Int<br> . IP Opr Pol Id InUse Pri Inh Int<br> .-------------------------------------------------------------------------------<br> .IRB_VXLAN1 1 No Up Master 100 1<br> . IPv4 Up n/a 100 No<br> . Backup Addr: 192.168.0.250<br> .IRB_VXLAN2 2 No Up Master 100 1<br> . IPv4 Up n/a 100 No<br> . Backup Addr: 192.168.1.250<br> .-------------------------------------------------------------------------------<br> .Instances : 2<br> .===============================================================================<br> |
So far the outputs look fabulous and we proceed further.
Case #2. Verification
First of all, we check connectivity between all VMs within these two domains:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 | <br> RP/0/0/CPU0:XR3#ping vrf VM1 192.168.0.1<br> Sun May 13 12:24:52.494 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.0.1, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms<br> !<br> !<br> RP/0/0/CPU0:XR3#ping vrf VM1 192.168.0.2<br> Sun May 13 12:24:54.923 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.0.2, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 159/289/409 ms<br> !<br> !<br> RP/0/0/CPU0:XR3#ping vrf VM1 192.168.1.1<br> Sun May 13 12:24:58.433 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms<br> !<br> !<br> RP/0/0/CPU0:XR3#ping vrf VM1 192.168.1.2<br> Sun May 13 12:24:59.553 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 249/327/399 ms<br> |
As you see, everything is working, what is a step forward comparing to interoperability tests between Nokia (Alcatel-Lucent) SR OS and Cumulus Linux, where we had some problems with ARP.
The most interesting case for me is that distributed anycast GW works into interoperable scenario. I’ve done two tests for that.
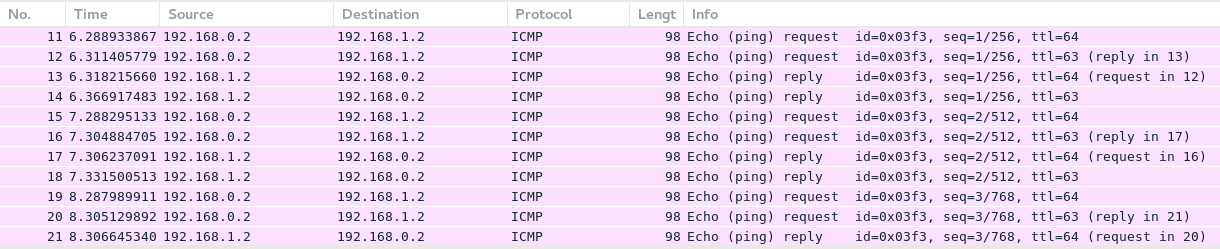
The first one is to ping VM3 from VM1 as both of them are connected to the same leaf switch SR1 and check what is going on in the wire:
1 2 3 4 5 6 7 | <br> RP/0/0/CPU0:XR3#ping vrf VM1 192.168.1.1<br> Sun May 13 12:54:30.912 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/9 ms<br> |
During this test we monitor with Wireshark all the links and see this traffic only on VLAN 111 and 333:

The second test touches VM2 and VM4, which are connected to vEOS2:
1 2 3 4 5 6 7 | <br> RP/0/0/CPU0:XR4#ping vrf VM2 192.168.1.2<br> Sun May 13 12:54:40.191 UTC<br> Type escape sequence to abort.<br> Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:<br> !!!!!<br> Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms<br> |
And again Wireshark shows the traffic only on interconnected links, which are VLANs 222 and 444:
Trace for ICMP over VXLAN is provided in article about Cumulus Linux interoperability
Here are the final configuration files of this lab: 120_config_final_XR3 120_config_final_XR4 120_config_final_SR1 120_config_final_VEOS2
Lessons learned
It was my first time working with Arista EOS, same as earlier with Cumulus Linux, and my main observations are the next ones.
First, CLI in Arista EOS is quite user friendly, so if I have forgotten to enter critical commands, it informs about it:
1 2 3 4 5 6 7 | <br> .vEOS2(config)#router bgp 65012<br> .! IP routing not enabled<br> .vEOS2(config-router-bgp)#exit<br> .vEOS2(config)#ip routing<br> .vEOS2(config)#router bgp 65012<br> .vEOS2(config-router-bgp)#<br> |
Second. another nice feature in Arista EOS allows us to check the configuration in the exiting context, exactly how we do in Nokia (Alcatel-Lucent) SR OS by issuing “info”:
1 2 3 4 5 6 | <br> .vEOS2(config-if-Vl222)#show active<br> .interface Vlan222<br> . vrf forwarding CUST<br> . ip address 192.168.0.254/24<br> . ip virtual-router address 192.168.0.250<br> |
Third, Arista also doesn’t share a lot of documentations, just as Nokia does. A lot of links I was trying to open at Arista website was telling me that I can’t access requested information as my level of the access is guest. In the time, when industry is moving into open-source networking, such approach looks weird for me.
Conclusion
Arista EOS is relatively new comparing to old giants like Nokia (merged with Alcatel-Lucent) or Cisco. And this is good, as they have great ideas and moving much quicker than mentioned companies. The same is relevant for Cumulus Linux, which is small and therefore moving forward at a good pace. But, what is more important for this particular article, we have reached the interoperability for all use cases between Nokia (Alcatel-Lucent) SR OS and Arista EOS, which looks very promising for data centre world. Take care and good bye!
P.S.
If you have further questions or you need help with your networks, I’m happy to assist you, just send me message. Also don’t forget to share the article on your social media, if you like it.
Support us
BR,
Anton Karneliuk
Useful links
During preparation of the article I have found very good article at Arista website about data centre fabric configuration, which I have used to study EVPN in Arista EOS.







