Hello my friend,
So far we have reviewed all main L2VPN MPLS services: VPWS, VPLS, PBB-EVPN. Now it’s time to review the joint operation of Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR for BGP/MPLS IP VPN (more commonly MPLS L3VPN) and get it working.
Brief overview
MPLS L3VPN is the most widely used service in the whole family of MPLS services. As it’s the most widely used, it’s also the clear and straightforward for the most part of network engineers. IPv4 VPN is covered in RFC 4364, and IPv6 VPN is covered in RFC4659.
From the high level prospective this service consist of BGP signaling (AFI/SAFI 1/128 for IPv4 and 2/128 for IPv6) and MPLS data plane. From the signaling point of view, we have the same attributes Route-Distinguisher (RD) and Route-Target (RT), what we have used in all type of BGP-based services (like VPWS or VPLS) previously. RTs should be the same across all PEs that participate in this VPN, whereas RD may be or may be not the same. Personally I prefer to use different RD for each and every PE/VRF because it adds possibility to have multipathing and load sharing in BGP/MPLS IP VPN. The disadvantage of such approach is higher memory utilization, so you must take care about this difference during deployment.
What are we going to test?
The good news is that here we can test data plane at Cisco IOS XRv now. You remember, we had the problem with data plane for L2 services (including L2 VPNs) at Cisco IOS XR in previous labs. Now this problem doesn’t bother us and we can perform all tests end-to-end between Nokia (Alcatel-Lucent) VSR (SR 77500) and Cisco IOS XR (ASR 9000).
The next point, which we are going to test, is operation of classical IP VPN for IPv4 and IP VPN for IPv6 that is called often 6VPE.
Topology
Physical topology remains the same for more than 10 labs already:
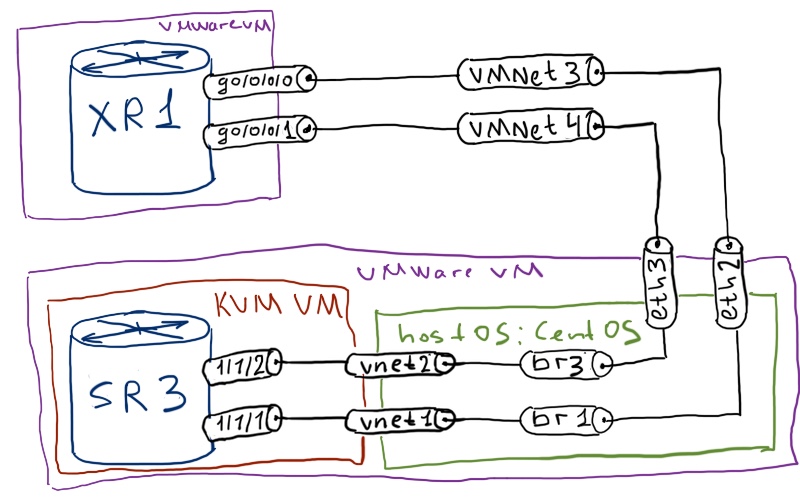
The logical topology is a little bit new. From the real world point of view, it makes no sense as we have single point of failure (SPOF) that is SR2. But we can imagine that there are two paths, which go through different P:
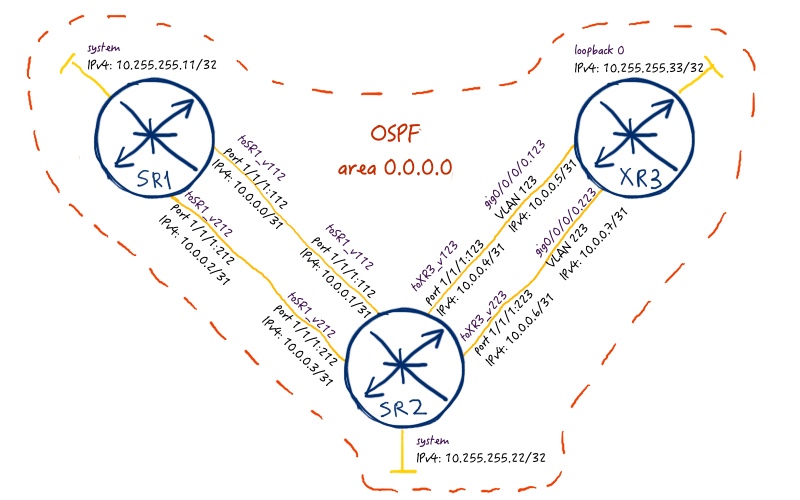
As IGP we use OSPF in our lab. For sure you can use ISIS, it’s up to you. But we have used ISIS previously in L2VPN’s labs, so this time I’m gonna using OSPF. For MPLS forwarding plane we will use MPLS LSPs built by RSVP-TE. There will be two tunnels in each direction for load balancing purposes.
Initial configuration for the lab is in the following files: linux_initial xr3_initial sr2_initial sr1_initial
MPLS forwarding plane
First of all let’s configure MPLS data plane for future BGP/MPLS IP VPN service. Take a look at the following picture:
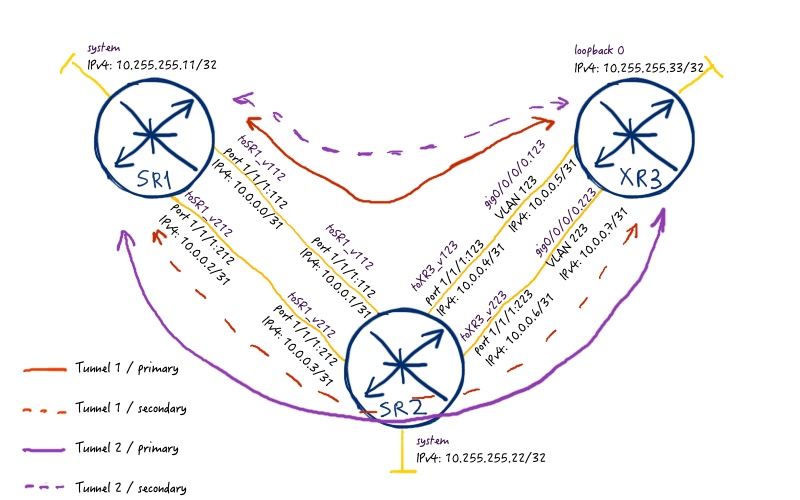
So we have to two tunnels in each direction between PE routers. They are built in the following ways:
- First tunnel between PEs goes only through links with admin-group (affinity) with value of 0x1 (include ZERO).
- Its secondary path (standby for Nokia (Alcatel-Lucent) SR OS) avoids these links (exclude ZERO).
- Second tunnel between PEs goes only through links with admin-group (affinity) with value of 0x2 (include ONE).
- Its secondary path (standby for Nokia (Alcatel-Lucent) SR OS) avoids these links (exclude ZERO).
The configuration is done only at PE routers:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR3 |
|
A:SR1>edit-cfg# candidate view |
RP/0/0/CPU0:XR3(config)#show conf |
Let’s briefly check our MPLS LSPs. In Nokia (Alcatel-Lucent) SR OS you should check first of all so called “tunnel-table”, what is the essence of all MPLS LSPs configured at your device:
|
A:SR1# show router tunnel-table |
We see that metric for both LSPs are the same, so they can load balance the traffic then. At Cisco IOS XR you see both LSPs in RIB:
|
RP/0/0/CPU0:XR3#show route ipv4 10.255.255.11 |
So we see that our MPLS tunnels are up and running and we can go further to the configuration of BGP/MPLS IP VPN itself.
For more details regarding LSP check refer to the MPLS/RSVP-TE article (link).
BGP/MPLS IPv4 VPN
Now we have approached the core topic of the article that is configuration of the VPN itself. The service map for our article is the following:
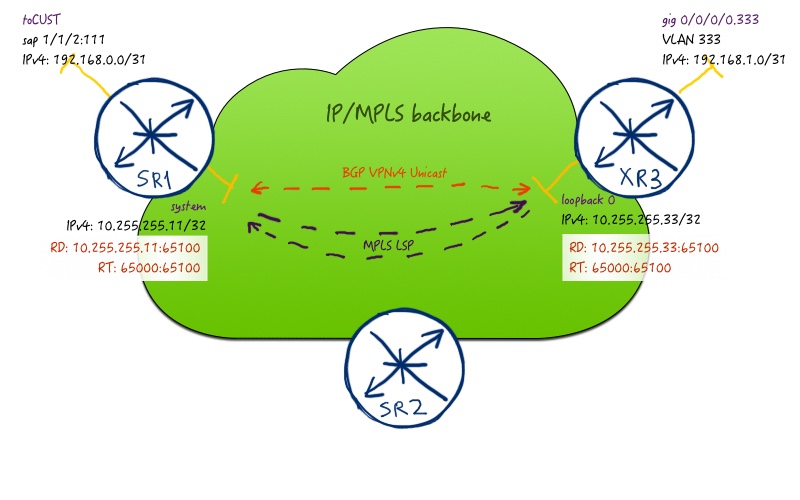
The configuration of VPN is necessary only at PE side, so we configure only SR1 and XR3:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR3 |
|
A:SR1>edit-cfg# candidate view |
RP/0/0/CPU0:XR3(config)#show conf |
Both in Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR we create first of all BGP peering for the address family VPNV4 (AFI/SAFI 1/128), because it’s basis for our IP VPN service. Then in Nokia (Alcatel-Lucent) SR OS we configure client’s port in access mode in order to be able to create SAP in VRF. Afterwards we create service VPRN 65100 (actually, VRF), where we configure corresponding route-distinguisher (RD) and route-target (RT), as well as interface to customer and customer’s BGP process.
In Cisco IOS XR we configure VRF and RTs in the global configuration context. Then we configure customer’s interface and associate it with VRF. The last step is the configuration of the BGP for this VRF including RD inside global BGP context.
If the logging is enabled, you will see in CLI the following messages, which inform you that BGP peering is built:
|
SR OS: |
As we don’t announce any routes still, we won’t see any prefixes in VRFs/VPRNs. We could announce interconnect prefixes, but usually it isn’t necessary in real deployment, so we don’t do it. What is possible to check at this stage is the peering of BGP in the corresponding address-family. From Nokia (Alcatel-Lucent) SR OS you do it as follows:
|
A:SR1# show router bgp summary |
In Cisco IOS XR you issue the following command:
|
RP/0/0/CPU0:XR3#show bgp vpnv4 uni summary |
It is also worth to check the router-distinguishers and route-targets associated with VPRN/VRF as this ensures you will have correct import/export of routes, when they will be announced. Here is the example from Nokia (Alcatel-Lucent) VSR (SR 7750):
|
A:SR1# show service service-using |
At Cisco IOS XRv (ASR 9000) you would use the following commands:
|
RP/0/0/CPU0:XR3#show vrf CUST_65100 detail |
Let’s add the life to our networks in terms of customer. Here is the topology of BGP/MPLS IP VPN service from the customer point of view:
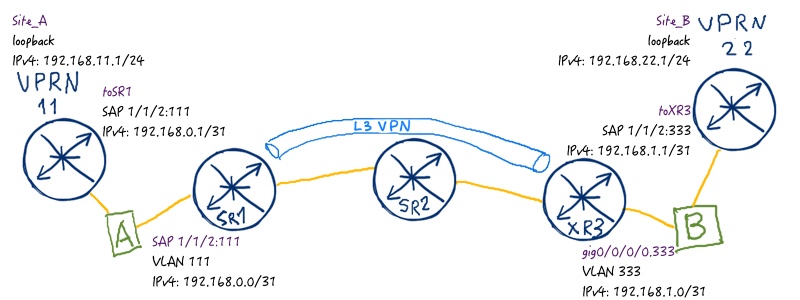
We are going to emulate customers using two VPRN instances at SR2.
Here you can find the final configuration files:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
A:SR1>edit-cfg# candidate view |
RP/0/0/CPU0:XR3(config)#show conf |
| VPRN 11 (SR2) | VPRN 22 (SR2) |
|
A:SR2>edit-cfg# candidate view |
A:SR2>edit-cfg# candidate view |
| Linux – bridge A | Linux – bridge B |
|
[root@localhost ~]# |
[root@localhost ~]# |
At customer routers (VPRN 11 and 22) we just configure local attached interface (emulated by loopback) that is announced via BGP. Remember that we have to configure explicit export policy in Nokia (Alcatel-Lucent) SR OS in BGP in order to announce any route. If you don’t configure them, no single prefix will be advertised. You see that configuration at VPRN 11 and 22 is almost identical.
In order to bring VPRN up you need to define route-distinguisher inside VPRN even in VRF-lite scenario in Nokia (Alcatel-Lucent) SR OS.
At our PE routers we just add specific route policies and BGP peering to the customer. In Nokia (Alcatel-Lucent) SR OS we add policy that allows redistribution of routes learned from MP-BGP to BGP session to customer. In Cisco IOS XR we need policy to allow advertisement routes to eBGP neighbor (by default Cisco IOS XR doesn’t send any routes to eBGP peers). Receiving policy isn’t obligation, but it should be configured as well.
Now we can check routing table at all our devices related to this particular BGP/MPLS IP VPN service. Let’s start with VPRN 11 (SR2) as first CE:
|
A:SR2# show router 11 route-table |
The next device in the flow (regarding to the provided image above) is the first PE that is SR1:
|
A:SR1# show router 65100 route-table |
Then comes the second PE XR3:
|
RP/0/0/CPU0:XR3#show route vrf CUST_65100 ipv4 |
And finally we comes to the second CE routers, which we have at VPRN 22 (SR2):
|
A:SR2# show router 22 route-table |
We see that our client’s prefixes from site A and B are installed in all corresponding routing tables along the path. At Nokia (Alcatel-Lucent) VSR SR2 that is one of the PEs you see that prefixes from Site B is available through MPLS LSP build by RSVP-TE. At Cisco IOS XRv XR3 that is another PE you see that prefix from Site A is known via BGP and is available through next hop in default routing table.
The next step is to check which service labels BGP has signaled for this VPN. In Nokia (Alcatel-Lucent) we have to issue two commands to check it:
|
A:SR1# show router bgp routes vpn-ipv4 |
In Cisco IOS XR you just issue one command and that’s it:
|
RP/0/0/CPU0:XR3#show bgp vpnv4 unicast vrf CUST_65100 labels |
You might spot that though we haven’t announces explicitly interconnect prefix between SR1 and VPRN 11 at SR2, we see it in BGP RIB at opposite router. This is the default behavior of Nokia (Alcatel-Lucent) SR OS, so you have to care of it.
Now it’s time to make some tests. Let’s perform ping from Customer’s Site A subnet to Site B subnet:
|
A:SR2# ping router 11 192.168.22.1 source 192.168.11.1 count 1 |
Here what shows us Wireshark at the path:
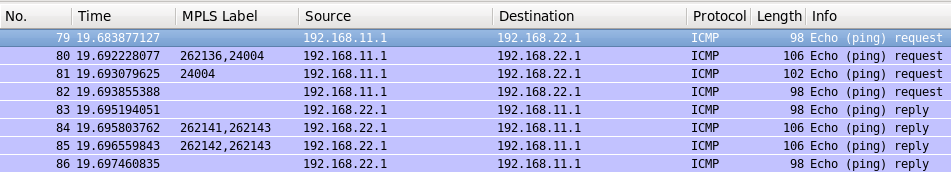
On the forward path from VPRN 11 to VPRN 22 you see PHP operation that is default for Cisco IOS XR (and other Cisco operation system). This PHP means that SR2 pops the transport label and sends the packet only with service label to XR3. In Nokia (Alcatel-Lucent) SR OS we don’t have such default behavior, so you see transport labels at both hops in MPLS core.
For more information about PHP and it’s configuration in Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR refer to the corresponding article.
BGP/MPLS IPv6 VPN
So far, so good. We have successfully implemented IP VPN service for IPv4 and we are going to do the same for IPv6. Such implementation is also often called 6VPE. Take a look at the image of the service:
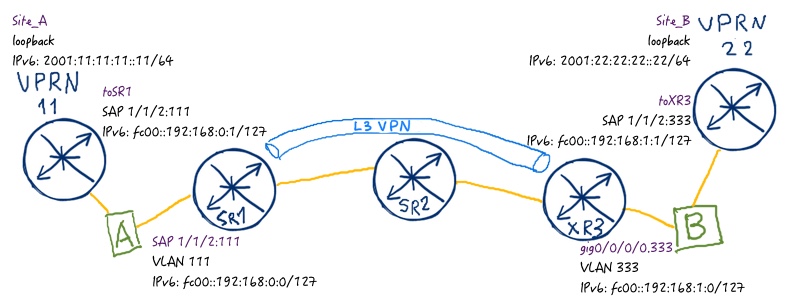
We won’t split configuration part for customer and core part here and will configure everything simultaneously. We use the same links for CE-PE peering, so there is no necessity to make additional configuration at linux:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
A:SR1>edit-cfg# candidate view |
RP/0/0/CPU0:XR3(config)#show conf |
| VPRN 11 (SR2) | VPRN 22 (SR2) |
|
A:SR2>edit-cfg# candidate view |
A:SR2>edit-cfg# candidate view |
In SR1 we don’t configure and apply new route-policy as it’s already attached during configuration of IPv4 part.
At PE routers we add vpnv6 unicast address-family at the peering between SR1 and XR3. Pay attention that in Nokia (Alcatel-Lucent) SR OS you have to mention all previous address families if you want to retain them, otherwise they will be deleted. In Cisco IOS XR you just configure new entity inside neighbor context. We also add IPv6 addresses at interfaces and configure BGP peering inside VRF/VPRN to IPv6 CE. In Cisco IOS XR we also add support of IPv6 unicast address family to VRF. In Nokia (Alcatel-Lucent) SR OS it’s done automatically.
At CE routers we just configure IPv6 addresses and add new entry into BGP policy in order to announce IPv6 prefixes.
Let’s check BGP peering and route table in VPRN 11 at SR2 that is Nokia (Alcatel-Lucent) VSR emulating CE:
|
A:SR2# show router 11 bgp summary |
As we have built two separate BGP sessions, we see both of them in “BGP summary”. In the route table you see that next hop for site B prefix is resolved to global unicast address (actually, site scope) prefix.
At first PE that is Nokia (Alcatel-Lucent) VSR SR1 router we’ll check BGP peering for core part in addition to route-table:
|
A:SR1# show router 65100 route-table ipv6 |
Here you see that we have only on BGP session for both address families (vpnv4 and vpnv6 unicast that is 1/128 and 2/128). It means that next hop lookup is the same for both address families and it’s resolved to MPLS LSP build by RSVP-TE. Let’s check BGP RIB as well (remember, we see here only received routes):
|
A:SR1# show router bgp routes vpn-ipv6 |
At Cisco IOS XRv PE that is our XR3 we see the same information but displayed in the different way:
|
RP/0/0/CPU0:XR3#show bgp vpnv4 uni summary |
We see advertised and received prefixes for both address families. Actually their amount is the same as we configure the same policies. I guess you might be interesting in what we see in the routing table and BGP RIB:
|
RP/0/0/CPU0:XR3#show bgp vpnv6 uni vrf CUST_65100 |
The next hop of the routes known from SR1 is “::ffff:10.255.255.11” and learned from default vrf. This is form of IPv4 address that you will always see, when IPv6 route is available over MPLS VPN.
Finally we check the routing table at VPRN 22 (SR2 CE):
|
A:SR2# show router 22 route-table ipv6 |
So far we have made a brief review of our tables and now we’ll perform the same ping test as we’ve done previously but this time for IPv6:
|
A:SR2# ping router 11 2001:22:22:22::22 source 2001:11:11:11::11 count 1 |
Wireshark shows us almost the same picture as above:
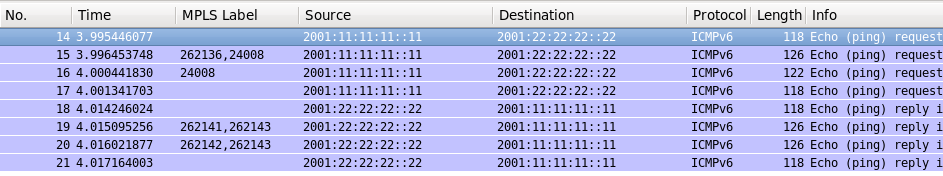
The only difference you might spot is that Cisco IOS XR allocates separate labels for IPv4 and IPv6 prefixes, whereas Nokia (Alcatel-Lucent) SR OS creates just one label for all prefixes associates with particular VPRN by default.
Final configuration is here: sr1_final linux_final xr3_final sr2_final
Lessons learned
During configuration of this lab I’ve faced very strange behavior of Nokia (Alcatel-Lucent) VSR, when newly configured BGP processes in VPRNs 11 and 22 weren’t sending any BGP packets so BGP peering with PE wasn’t established. I’ve tried to make some reconfiguration but there was no success. Then I’ve restarted that VSR and everything started working as proper. As Germanys say “Reboot tut gut”, what means in English “reboot makes good”.
Conclusion
Comparing to the MPLS L2VPN services, configuration of MPLS L3 VPN (BGP/MPLS IP VPN) is much simpler and shorter. Basically you need only route distinguishers and route targets, which were necessary in all BGP-based L2 VPN services as well. All features, which we have reviewed from the beginning of our journey into joint operation of Nokia (Alcatel-Lucent) SR OS / Cisco IOS XR world, allows us to build middle-size network for service provider. In the next articles we’ll discover some advanced features that help you to build high scalable network. Take care and good bye!
Support us
BR,
Anton Karneliuk






