Hello my friend,
BGP is the routing protocol that I like most of all. Really, it’s possible to use solely BGP to cover all internal and external routing scenarios. BGP is so powerful and feature-rich that it’s impossible to cover all the topics in a single article that’s why in this article I’ll focus on usual IPv4 and IPv6 address families (sometimes it’s called vanilla BGP).
Topology
For those of you, who follow my series of articles, the physical topology is already familiar and probably it isn’t necessary to remind it. For those of you, who are reading my article for the first time, topology consists of Nokia (Alcatel-Lucent) VSR and Cisco IOS XRv:
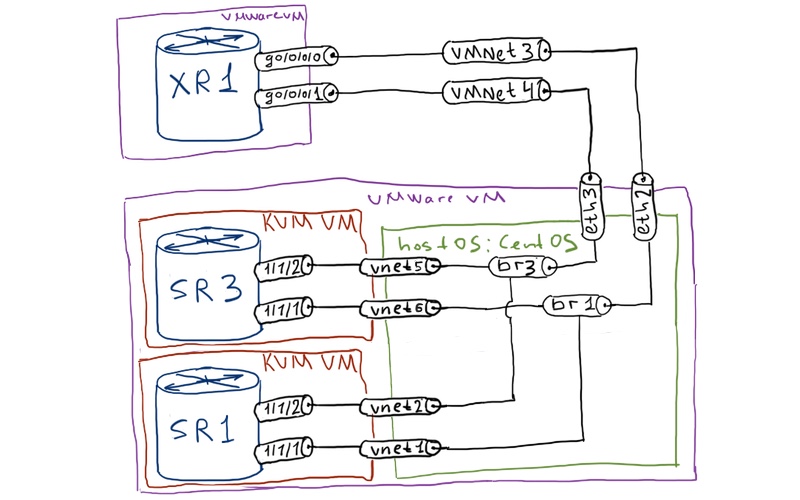
On top of the physical topology some trunks are created in a creative way that forms the following logical topology:
You might be wondering, how it appears that we have only three physical (actually virtual, but it isn’t the case) devices and at the logical topology there are 5 routers. Well, I use simple trick that is called virtualization to create VRFs at Nokia (Alcatel-Lucent) VSR and at Cisco IOS XRv, which I used previously describing IPv6/OSPFv3. From routing point of view VRF is a fully independent router, what fits my idea to make BGP topology more interesting very well. The initial configuration files for the lab you can find here: linux SR1_initial SR3_initial XR1_initial
Basic BGP connectivity for IPv4 unicast
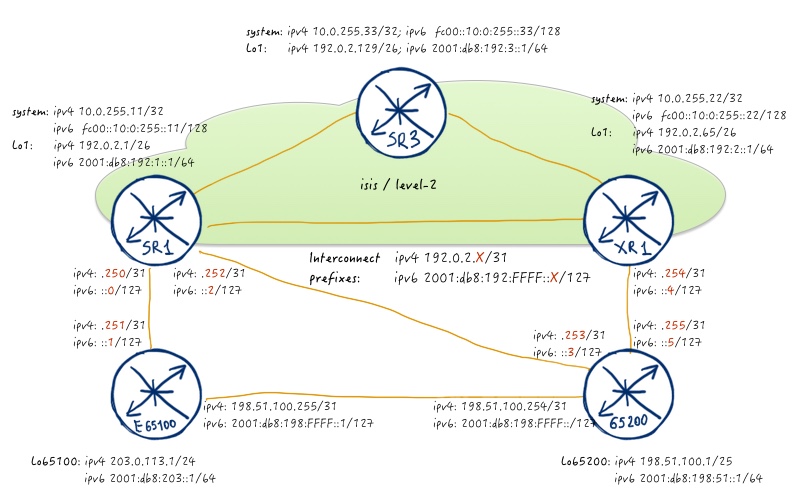
I think you know BGP basics and theory of its operation, so I won’t explain its details. Take a look at the BGP topology below:
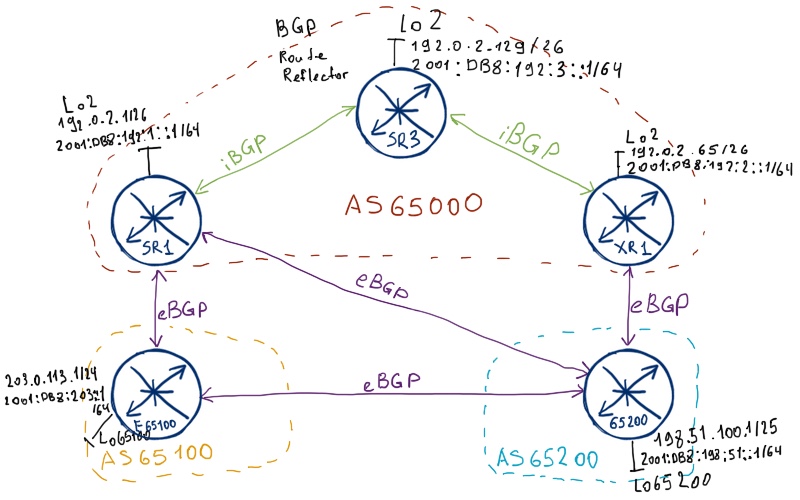
Before proceeding with the configuration, let’s briefly review, what we actually should configure. Three routers SR1 (Nokia (Alcatel-Lucent) SR OS), SR3 (Nokia (Alcatel-Lucent) SR OS) and XR1 (Cisco IOS XR) form AS 65000 and they have iBGP (internal BGP) peering in the following way:
- SR3 is route reflector (RR) and it forms peering both with SR1 and XR1;
- SR1 and XR1 forms peering only with SR3; they don’t form peering with each other;
- iBGP peering is built between system interfaces and loopback 0 IPv4 addresses;
- SR1 and XR1 changes next-hop path attribute to its system/loopback0 address, when they announce it to route reflector SR3 (next-hop-self);
Routers E65100 (VRF at Cisco IOS XR) and 65200 (VPRN at Nokia (Alcatel-Lucent) SR OS) are eBGP (external BGP) peers to AS 65000 and each resides in its own AS: E65100 in AS 65100 and VPRN 65200 in AS 65200. All eBGP sessions are built at directly connected IPv4 addresses.
In terms of prefix announcement (or more correct term for BGP is NLRI – Network Layer Reachability Information) each router announces public IPv4 address associated with its loopback interface (loopback1, loopback 65100 or loopback 65200). First of all we’ll configure internal BGP (iBGP):
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
| SR3 (route reflector) | XR1 (how RR configuration looks like) |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
So, basically we do three things here:
- create redistribution profile for BGP routes, which we want to send/receive including redistribution of local loopback1 into BGP;
- configure internal BGP peering (what is actually TCP session on port179) between routers in AR 6500;
- apply redistribution profile to BGP configuration;
- add cluster X.X.X.X command under group configuration in BGP at route reflector (configuration for route reflector in Cisco IOS XR is provided only for reference and it isn’t applied actually).
In the initial configuration of SR1 and SR3 you can see that we have enabled logging of BGP events to console. If you have questions how to do it, read this article.
When everything is configured properly, we’ll see immediately sessions coming up. Both Nokia (Alcatel-Lucent) VSR (SR 7750) and Cisco IOS XR (ASR 9000) inform us about it:
|
SR OS: |
If logging isn’t configured or you have missed it somehow, use the following command for verification (actually BGP troubleshooting always start with it). For Nokia (Alcatel-Lucent) SR OS:
|
A:SR3# show router bgp summary |
You can spot here a lot of valuable information. Mainly everything is 0 as we have configured only one address family (IPv4 unicast). Actually you this information in the end of output, where neighbors and activate families are listed. For Cisco IOS XR each summary are address family specific, so you have to mention it, when you want to check peering status:
|
RP/0/0/CPU0:XR1#show bgp ipv4 unicast summary |
BGP has quite complex state machine that describes different state of adjacency. In general if you see something besides timers in column “Up/Down”, it’s bad. It’s bad, because it means that adjacency isn’t established. Sometimes it might be desired behavior if you have manually disabled the neighbor (it will be as Admin down or idle).
Now we come to the point of fundamental difference in BGP implementation between Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR. To be honest, as I has grown up together with Cisco, its outputs seems to me more logical and less confusing. But probably it’s just the matter of taste. So, let’s take a look at BGP RIB at Cisco IOS XR:
|
RP/0/0/CPU0:XR1#show bgp ipv4 unicast |
You see here 3 IPv4 prefixes announced by SR1, XR1 and SR3 routers. Prefix “192.0.2.64/26” is locally redistributed by route policy and it has next hop of “0.0.0.0” and weight 32768.
For those of you, who aren’t familiar with Cisco, weight is Cisco proprietary path attribute that is local to the router (not announced to anyone) and considered with the topmost priority in path selection process (prior to RFC based local preference).
Also point out that upon redistribution Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR set different origin codes to routes (SR OS – igp and IOS XR – incomplete). Cisco has another mechanism of prefix announcement besides redistribution, which sets origin to igp as well. I’ll describe it later. Now let’s see in the Nokia (Alcatel-Lucent) SR OS BGP RIB at SR3:
|
A:SR3# show router bgp routes ipv4 |
That’s what makes me crazy. In BGP RIB in Nokia (Alcatel-Lucent) SR OS you see only received routes from other peers. It doesn’t show BGP routes that you originate locally. So actually the output below corresponds to Adj-RIB-In (database with incoming routes from other routers) If you don’t know this fact, you will spend a lot of time troubleshooting BGP at this platform. You can see local routes only in Adj-RIB-Out table per specific neighbor:
|
A:SR3# show router bgp neighbor 10.0.255.22 advertised-routes |
As per RFC4271 there are 3 RIB: Adj-RIB-In, Adj-RIB-Out and Loc-RIB. Reference this RFC for more details.
So take care about this difference as it’s very important. Also such difference has another important consequence, which is obvious at SR1:
|
A:SR1# show router bgp routes |
You see that Nokia (Alcatel-Lucent) router SR1 see its own route in BGP RIB reflected by SR3:
|
A:SR1# show router bgp routes 192.0.2.0/26 detail |
As you can imagine Cisco IOS XR has very similar command to check details of the routes:
|
RP/0/0/CPU0:XR1#show bgp ipv4 uni 192.0.2.0/26 |
The main differences between these two outputs is that Nokia (Alcatel-Lucent) SR OS shows the original path attributes of incoming IPv4 prefix and path attributes after processing by ingress route-policy (we don’t have it configured, so they are equal).
Let’s configure external BGP (eBGP). Here is the image for your reference:

The configuration will be as follows:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>bgp# info |
RP/0/0/CPU0:XR1(config)#show conf |
| 65200 (VPRN at SR3) | E65100 (vrf at XR1) |
|
*A:SR3>config>router>policy-options# info |
router bgp 65000 |
VRF at Cisco isn’t fully separated instance, because it inherits AS number from parent BGP context. That’s why in order deceive peering BGP routers, we configure local-as 65100 for BGP peering at E65100 router. On the other hand we have also to deceive E65100 logic by configuring local-as 65535 at SR1 in direction of E65100. In Nokia (Alcatel-Lucent) it’s easier: we just configure AS number under VPRN configuration at SR3. Such tricks are needed only due to VRF usage as eBGP neighbors.
The implication of the explanation above is to make the router think that he peers with router in another AS rather than AS, where the router really resides. It also changes the AS PATH attribute of the BGP routes. Besides this fact, other configuration is very straightforward. Just pay attention that Cisco IOS XR requires to have both ingress and egress route policies configured for eBGP neighbors (there is no such requirement for iBGP). We’ve configured md5 authentication between all external BGP neighbors in order improve security.
Let’s check the routing table at different routers. Nokia (Alctel-Lucent) VSR (SR 7750) in AS 65200 has the following BGP Adj-RIB-In:
|
A:SR3# show router 65200 bgp routes |
Due-to local-as 65535 configurations at SR1 in direction of E65100 some routes seem to be originated from or passing by AS 65535 instead of real AS 65000.
You see that 65200 (VPRN at SR3) has in its BGP RIB three copy of each route, sourcing from XR1, SR1 and E65100. Nevertheless only one route is marked with “u” meaning that this route is installed in routing table:
|
A:SR3# show router 65200 route-table protocol bgp |
The BGP RIB and routing table for E65100 (vrf at XR1) looks as follows:
|
RP/0/0/CPU0:XR1#show bgp vrf E65100 ipv4 unicast |
In order to reduce the length of the article I put connectivity test in the separate file. You can refer to it, if you want to check it:
Comprehensive theory about route policies in BGP
In both Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR route policies are actively used for almost all tasks. For example, route redistribution, modification of path attributes and filtering of incoming/outgoing prefixes, filtering what is to install into routing table and many other things. But there is a significant difference how these routing policies work. Let’s start with Nokia (Alcatel-Lucent) SR OS.
Route policy in Nokia (Alcatel-Lucent) SR OS
In Nokia (Alcatel-Lucent) we have just two route policies, which control whole operation of BGP. It’s export and import policy:
- Export policy chooses appropriate prefix from routing table (not BGP RIB) based on selection criteria (configured under “from” section) and apply action to the route (configured under “action” section). If the action is “reject”, then such route isn’t sent to neighbor. If the action is “allow”, the route is sent and you have possibility to modify its path attributes.
- Import policy is used for modification of path attributes for incoming routes and filtering their installation in routing table. In any case the routes will be in BGP RIB (Adj-RIB-In, actually).
There are three possible points (Cisco IOS XR calls it attach point), where you can apply routing policy:
- In case of BGP configuration mode these policies will be used for prefixes send/receiving to/from all BGP neighbors.
- In case of group sub mode in BGP these policies will be used for prefixes send/receiving to/from BGP neighbors within this group
- In case of neighbor sub mode in BGP group these policies will be used for prefixes send/receiving to/from particular BGP neighbor
Pay attention that there is no inheritance between policies. Only one export and one import policy will be used (for all address families), meaning that actions from only one policy per destination will be applied to the prefix. The order of applying is from more specific to less specific:
- neighbor’s import/export policy;
- group’s import/export policy;
- global BGP’s import/export policy.
Due to the fact that only one policy is used, you should be very careful with filtering what and how you want to announce.
There is also possibility to influence path attributes of outgoing prefixes in Nokia (Alcatel-Lucent) SR OS by configuring certain parameters under group or neighbor configuration sub modes.
Route policy in Cisco IOS XR
Contemporary to Nokia (Alcatel-Lucent) SR OS, Cisco IOS XR has strong decoupling between:
- population of Loc-RIB by local routes;
- filtering prefixes and manipulation their attributes during sending/receiving them to BGP peers;
- filtering what should be installed in routing table.
One way of population of Loc-RIB in BGP is done via redistributing with route-policy or with network statement. Another way is via getting prefixes from BGP neighbor. In this case you can use ingress route policy for filtering routes and modification of their path attributes before adding them to Loc-RIB. Such route policy is applied per neighbor (or per group of neighbors) per address-family.
If the prefix is got from BGP neighbor, after installing it in BGP Loc-RIB it will be analyzed in order to be installed in routing table. Here filtering can be done using table-map route policy. If it satisfies criteria and it is the best route, it will be installed in routing table then.
Best routes are also advertised to BGP neighbors. The egress policy route is used for filtering and modification of path attributes for routes being advertised. Such route policy is also applied per neighbor (or per group of neighbors) per address-family.
On the examples further (during configuration of IPv6 unicast address family or upon traffic engineering) pay attention to the differences in configuration of route-polices.
BGP connectivity IPv6 unicast
So far we have reviewed IPv4 unicast operation of BGP and how in general route policies work. Both these knowledge are necessary for us right now in order to configure IPv6 unicast address family. We’ll configure it simultaneously for all BGP peering (internal and external). The task is the same of what we have in IPv4 in terms of policies and peering.
Before we proceed with the configuration, just briefly review one important point. BGP peering is established over TCP session. For TCP session some IP addresses are used (we have used IPv4 in the part above). So you have two options how to add IPv6 routing to BGP:
- Add IPv6 unicast address family to existing IPv4 peering. In this case you have to manipulate next-hop with route policies, as it isn’t adjusted automatically.
- Establish new TCP session (new BGP neighbor) between IPv6 addresses for IPv6 unicast address family
Both of these options have advantages and drawbacks. The first option reduces the number of sessions, but increase complexity of route policies for next hop control. The second option makes IPv4 and IPv6 completely independent, but increases the number of sessions that need to be managed.
In our task we’ll configure separate IPv6 peering for external BGP and reuse existing IPv4 peering for internal BGP applying appropriate route maps.
Pay attention that adding new address family to existing BGP peering leads to reestablishment of the peering for IPv4 unicast address family as well. Be very careful upon configuring it in production network.
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
| SR3 | E65100 (vrf at XR1) |
|
*A:SR3>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
| 65200 (VPRN at SR3) | |
|
*A:SR3>config>router>policy-options# info |
The configuration part was quite long due to bug amount of configuration entries. Stay here for a while, as here you can see the huge difference that was described previously in route policy theory. In Nokia (Alcatel-Lucent) SR OS you have one route policy for all address families per attach point. That’s why we necessary entries in route policy, which was used for IPv4 previously. In Cisco IOS XR you configure route policy per address family separately, and for me it seems easier. Also you can find that besides IPv6 address in neighbor statement, there is no difference in configuration of BGP for IPv6 address family.
During applying of the configuration you will see that IPv6 or IPv4/IPv6 BGP peering comes up:
|
SR OS: |
For IPv4 AFI (Address Family Indicator) is 1 and for IPv6 AFI is 2. SAFI (Sub Address Family Indicator) 2 means “unicast”. For more information attend to IANA
Pay attention that Nokia (Alcatel-Lucent) VSR (SR 7750) doesn’t tell you for which AFI/SAFI the neighboring comes up. You can check it in the BGP summary table:
|
A:SR1# show router bgp summary |
At the output above with the bold marked the follofing:
- BGP peering between SR1 and SR3 for IPv4 and IPv6 unicast is built on top of IPv4 session. So there is one TCP session for which two AFI/SAFI groups are negotiated
- BGP peering between SR1 and E65100 consists of two different TCP sessions (actually there are two different BGP neighbors), where each session is used for only one AFI/SAFI.
In Cisco IOS XR the BGP summary table is built per AFI/SAFI, so you should use two commands to check it:
|
RP/0/0/CPU0:XR1#show bgp ipv4 unicast summary |
Next important part of network operation (and for IPv6 as well) is RIB. Let’s see what we have there at Nokia (Alcatel-Lucent) SR OS router in routing table:
|
A:SR1# show router route-table ipv6 protocol bgp |
Take a look at next-hop field. It’s resolved to IPv6 link local address of the peer, if the prefix is learned from internal BGP (iBGP) neighbor. Nevertheless in BGP RIB you see original next hop, what is advertised by neighbor:
|
A:SR1# show router bgp routes ipv6 2001:db8:192:2::/64 |
So Nokia (Alcatel-Lucent) SR OS automatically makes RIB optimization in order to improve packet forwarding and simplify RIB/FIB lookup. If we’ll take a look into FIB, what is actually used for traffic forwarding, you’ll see the same picture in terms of next hop:
|
A:SR1# show router fib 1 ipv6 2001:db8:192:2::/64 |
What is about Cisco IOS XR routing table?
|
RP/0/0/CPU0:XR1# show route ipv6 bgp |
You see that next hop in routing table is just the same as it’s in BGP RIB:
|
RP/0/0/CPU0:XR1# show bgp ipv6 unicast 2001:db8:192:3::/64 |
Nevertheless Cisco IOS XR makes the FIB optimization as well, where you see actual information for packet forwarding:
|
RP/0/0/CPU0:XR1#show cef ipv6 2001:db8:192:3::/64 detail |
In order to reduce the length of the article I don’t provide the output of ping tests. You can perform them yourself. Don’t forget to mention correct source, which is advertised via BGP.
Prefix aggregation in BGP
Usually you don’t want that external neighbors see the details of your network. Another important point here is that the there is strict regulation in Internet routing, what states that the maximum prefix length in Internet routing table must be 24. All routes with longer prefixes must be aggregated at least to /24 subnet. Let’s advertise from SR1 (Nokia (Alcatel-Lucent) SR OS) and XR1 (Cisco IOS XR) only aggregated IPv4 192.0.2.0/24 and IPv6 2001:db8:192::/48 prefixes to their external BGP (eBGP) neighbors:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
Both Nokia (Alcatel-Lucent) SR OS and Cisco IOS XR have possibility to add key “summary-only” to aggregation command. It will effectively filter from announcement all routes that fit aggregation subnet and therefore only aggregated route will be announced. It will filter also actual Lo1 prefix from advertisement to iBGP neighbors and will create partial traffic drop (when traffic to Lo1 of SR1 will come to XR1, for example). In our case we don’t want it, so we don’t issue it. Also pay attention that in Nokia (Alcatel-Lucent) SR OS you choose “protocol aggregate”, which differs from the protocol that you have used before.
Let’s check the routing tables at E65100 (vrf at XR1) before implementing the configuration above and after that:
|
Before aggregation at SR1/XR1: |
The same picture you can observe at 65200 (VPRN at SR3):
|
Before aggregation at SR1/XR1: |
You can see that right now only the aggregated routes (one for IPv4 and one for IPv6) present in routing table at external BGP (eBGP) neighbors for AS 65000, whereas at SR3, which is internal BGP (iBGP) neighbor, you see both aggregated routes and original Lo1 prefixes from SR1 and XR1.
|
A:SR3# show router route-table ipv4 protocol bgp |
BGP path selection algorithm
BGP has a numerous path attributes that influence selection of the best route, which is installed in the routing table. These attributes are processed in the strict order, described in RFC4271.
In addition to RFC Cisco IOS XR (as well as Cisco IOS, IOS XE and NX-OS) has two more steps. The very first step in Cisco IOS XR called “weight”, what is Cisco-specific path attributes. This attribute is set to 32768 to routes that is originated by route (via network, redistribution or aggregation) and 0 to routes learned from BGP neighbors. The route with the biggest numerical number is chosen as the best one. Weight is local to the router and isn’t advertised to the peers.
Another Cisco-specific step is called “Locally originated”. Cisco IOS XR prefers routes that are originated locally to routes learned from neighbors. This step comes between local-preference and AS_PATH. Take a look at Cisco BGP path selection attribute.
Each of BGP path attributes can be installed with route-policy either in incoming or outgoing direction. Make yourself feel comfortable with this algorithm in order to understand why certain routes are chosen as the best one.
To show the example of this algorithm we’ll configure the following routing policy in AS 65000:
- All traffic destined to AS 65200 must pass link between XR1 and 65200 (VPRN at SR3).
- All traffic destined to AS 65100 must pass link between SR1 and E65100 (VRF at XR1).
To achieve the desired task we need to apply the following configuration to our routers:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
What we are doing in these route policies is filtering increasing the local-preference BGP path attribute of the prefixes are originated in neighboring AS based on the task above. Let’s check the routing table at Nokia (Alcatel-Lucent) SR OS router SR1 for BGP routes:
|
A:SR1# show router route-table ipv4 198.51.100.0/25 |
You see that now route to IPv4 prefix 198.51.100.0/25 points to XR1, though it has a direct link to AS 65200. In BGP RIB at SR1 you can see that there are several possible next hops for IPv4 prefix 198.51.100.0/24 and the best one is chosen by the highest local preference:
|
A:SR1# show router bgp routes ipv4 198.51.100.0/25 |
The same picture for prefixes from AS 65100 you can see at Cisco IOS XR:
|
RP/0/0/CPU0:XR1#show route ipv6 bgp |
Local-preference is applied usually to the incoming route updated and influences the egress traffic from your network. You can see that in routing table of 65200 IPv4 prefix 192.0.2.0/24 is accessible via oldest stable route:
|
A:SR3# show router 65200 bgp routes ipv4 192.0.2.0/24 |
To influence ingress traffic from the peering AS to your network other path attributes must be used (AS_PATH prepending, ORIGIN or MED) with route-policy in outbound direction. Usually AS_PATH manipulation is used, because it’s the strongest path attribute across all the rest. I won’t provide any example here, but in the next session you will see the example how else it’s possible to influence.
BGP Communities
BGP has very powerful tool for traffic engineering (and not only) that is called communities. In a few words we can describe BGP community as a tag, which is added to certain routes, when they are advertised to the neighbors. On the receiving side you can match routes by this tag and apply necessary actions. It’s much more convenient than matching routes solely by IPv4/IPv6 prefix, because you can create more flexible and simple route policies.
In Cisco IOS XR you can set community also during redistribution of routes into Loc-RIB from routing table.
There are two main different types of communities: standard and extended. Extended communities are used for all types of BGP/MPLS VPN solutions (both L2 and L3). The most widely used extended community is route-target, which is corner stone of BGP/MPLS VPN. Standard communities are used for all types of address families and don’t have any specific function. So their use is totally up to engineers.
In this article I’ll cover one example of using standard community path attribute. This application is described in RFC1998 and provides the way for the customer to influence incoming traffic for the customer.
This RFC isn’t mandatory so it might be not implemented by your peering BGP AS. Check with your ISP if it’s implemented and how it’s implemented, before making any configuration in live network!
To make it shorter, mentioned RFC provides the way of setting the local-preference based matching standard community in ingress route-policy. In such a way customer can influence how traffic from its ISP should come into customer’s network. So it’s possibly to perform maintenance work at routers without any traffic disruption by smoothly rerouting the traffic between your routers.
We’ll implement the following routing policy at E65100 and 65200:
- Prefixes coming with community x:60 become local-preference 60;
- Prefixes coming with community x:70 become local-preference 70;
- Prefixes coming with community x:80 become local-preference 80;
- Prefixes coming with community x:90 become local-preference 90;
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
RP/0/0/CPU0:XR1(config)#show conf |
|
| 65200 (VPRN at SR3) | E65100 (VRF at XR1) |
|
*A:SR3>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
In Nokia (Alcatel-Lucent) SR OS sending and receiving of communities is configured by default. Cisco IOS XR sends community to iBGP neighbors by default, and for eBGP neighbors you have to configure it explicitly. In order to check whether our solution work, let’s configure the distribution of IPv4 aggregate route from AS 65000 with community 65000:60 from SR1 and 65000:80 from XR1:
| Nokia (Alcatel-Lucent) VSR (SR 7750) | Cisco IOS XR (ASR 9000) |
| SR1 | XR1 |
|
*A:SR1>config>router>policy-options# info |
RP/0/0/CPU0:XR1(config)#show conf |
Pay attention that in Nokia (Alcatel-Lucent) SR OS you configure community entry and in route-policy you mention that entry. In the case above they are the same but the first “65000:60” is name of the entry and the latter is the actual numeric value of the community.
You can see that the traffic to IPv4 prefix 192.0.2.0/24 will be sent to XR1 now and this decision is precise (not sporadic):
|
A:SR3# show router 65200 bgp routes ipv4 192.0.2.0/24 |
In the details of this prefix you see how local preference is changed based in the community value:
|
A:SR3# show router 65200 bgp routes ipv4 192.0.2.0/24 detail | match expression “Comm|Local|Original|Modified” |
In general from E65100 traffic to 192.0.2.0/24 should go through 65200 (VPRN at SR3), but due to the fact that it’s just VRF with parent BGP process in AS 65000, it just drops routes originated in AS 65000, therefore advertisement from 65200 is dropped at E65100.
The final configuration files you can find here: SR1_final SR3_final XR1_final
Lessons learned
The main lessons learned for me was the difficulty to make the article compact. There are lots of interesting books about BGP written by Alcatel-Lucent, Cisco, Juniper and other vendors that in depth explain the operation of the protocol and configuration in that vendor’s OS. I advise you to find any book with BGP theory and then attend to my article if you have difficulties with BGP theory.
Conclusion
BGP is very good and useful protocol in modern network. In SDN environment it even tends to remove all other routing protocols due to its unprecedented flexibility caused by path attributes and address families. Probably my review was quite brief, but my target isn’t teaching you BGP basics. I want to share with you configuration pattern from basic to advanced level in multi vendor environment. In my series in the future I’ll cover other BGP features that also very useful and used in current networks. Take care and good bye.
Support us
BR,
Anton Karneliuk





hi Anton
Let me congratulate you for such a creative labs, I just got some questions or doubts about it
1.-Finals configs are the final configs? it is just that some parameters were missing according to your design. for example in SR1 It is supposed to be connected with SR2 and XR, but if you take a look in final configs you only use a port, same situation from XR to S1 in IGP.
2.-I tested all your labs Timos 12, but in connection from SR1 to SR3 when you add to a vprn ask for access port.
It seems that you got another final configuration, but anyway, I faced a couple hours becasue I translate all your labs to cisco IOS to save power in my Lab, I dont have a server.
Regards
Hi Hugo,
Usually final configuration is final configuration. I’ll double check the configuration for you.
BR,
Anton
Hi Hugo,
I’ve tested this configuration using TiMOS 12 and running it on EVE-NG in my laptop (i7 with 16GB of RAM). I tested it with 3 SR-OS router (I didn’t use XRv because somehow it run very slow in EVE-NG) with the following topology:
SR3
/ \
SR1 ——— SR2
And in my opinion there is nothing wrong with the configuration.
And to make it works, I turned all ports into hybrid mode, so the port can be attach to either routerinterface or SAP at VPRN
Best Regards
hi Anton,
I am a big fan of your blog, really so much to learn about Service Provider networks (MPLS and its Services) from this blog.
I have question regarding the “expression” when we create BGP policy, could you explain what are they used for ?
I try to googled it and found the following links:
https://infoproducts.alcatel-lucent.com/html/0_add-h-f/93-0074-HTML/7750_SR_OS_Routing_Protols_Guide/route_policies.html
But still I cannot comprehend, why we need this expression when we create policy for BGP attributes (such as as-path, community, etc).
Best Regards
Hello Fakhri,
Thanks for kind feedback.
If you refer to regular expressions, they are widely used across all vendors (Nokia, Cisco, Junier, Huawei and so on). This is the sophisticated methos of route filtering, which can be applied to path attributes you have mentioned: AS-PATH community and so on. For example, instead of creating list that matches the whole AS-PATH, you can just prefer routes coming through certain AS and so on.
More info: https://tools.ietf.org/html/rfc1164 and https://tools.ietf.org/html/rfc1998
BR,
Anton
Hello Anton!! I liked very much your aarticle!
My name is Renato and we work in a Telecom Company. We are change the our BGP router and I would like to know how brand you consider the best in BGP work, Huawei, Nokia, Juniper or Cisco?
We receive commercial propouse for SR-01, Juniper MX-10003 and Huawei NE8000-M14 and ZTE M6000-8S Plus.
Hello Renato,
Thanks for your message. I think it is all down to your requirements:
– which functionality (IPv4/IPv6, MPLS, PIC, AddPath, etc)
– how many routes
– which amount of traffic you need to pass and so on.
Also, for sure, the commercial aspect would be important, as different companies would offer different models (someone may have high purchasing price but predictable support costs, whereas with others it may not that obvious with seemingly low prices).
If you are interested, you can use our consulting services so that we can help you to work out the solution: https://training.karneliuk.com/individual-training/
Best,
Anton